Updated:July 16th, 2020
Is your WiFi stolen? You would like to know the best programs to check if someone is using your WiFi network and how to kick him out.
Do you want to find out who is connected to your WiFi network? What devices are they using and what are their IPs? Do you think that your neighbors are stealing your WiFi? Find out here how to prevent your WiFi from being stolen.
Wi-Fi technology is everywhere and almost all electronic devices have a wireless network connection. However, setting up a wireless network also presents some problems when it comes to a home network and the devices connected to it.
Naturally, creating your own Wi-Fi network with adequate protection like WPA2 and a strong password is vital, but it does not ensure that outsiders are not using your network without your knowledge . Chances are, friends, neighbors, or family members have shared your WiFi credentials with others, and people you don’t even know, have access to your network and shared files.
There are many simple tools that help find out who is connected to your wireless network.
The simplest way to find out which devices are connected to a Wi-Fi network is using analysis software , available for the main platforms. The user will be able to see a list of all connected devices and easily identify them and eventually block them.
Read: How to Lock Down Your Home Network
Therefore, it is essential to protect the home network, implementing different strategies to, among other things, avoid “intruders”.
Programs to check who is connected to your WiFi network
A lot of modern routers will give you a list of the wired and wireless devices that make a connection to the network, but others don’t and some people don’t really know how to find that information. You will find below some tools to get the list of connected devices in your network.
Read: Ways to Know Who Is Tracking You Right Now
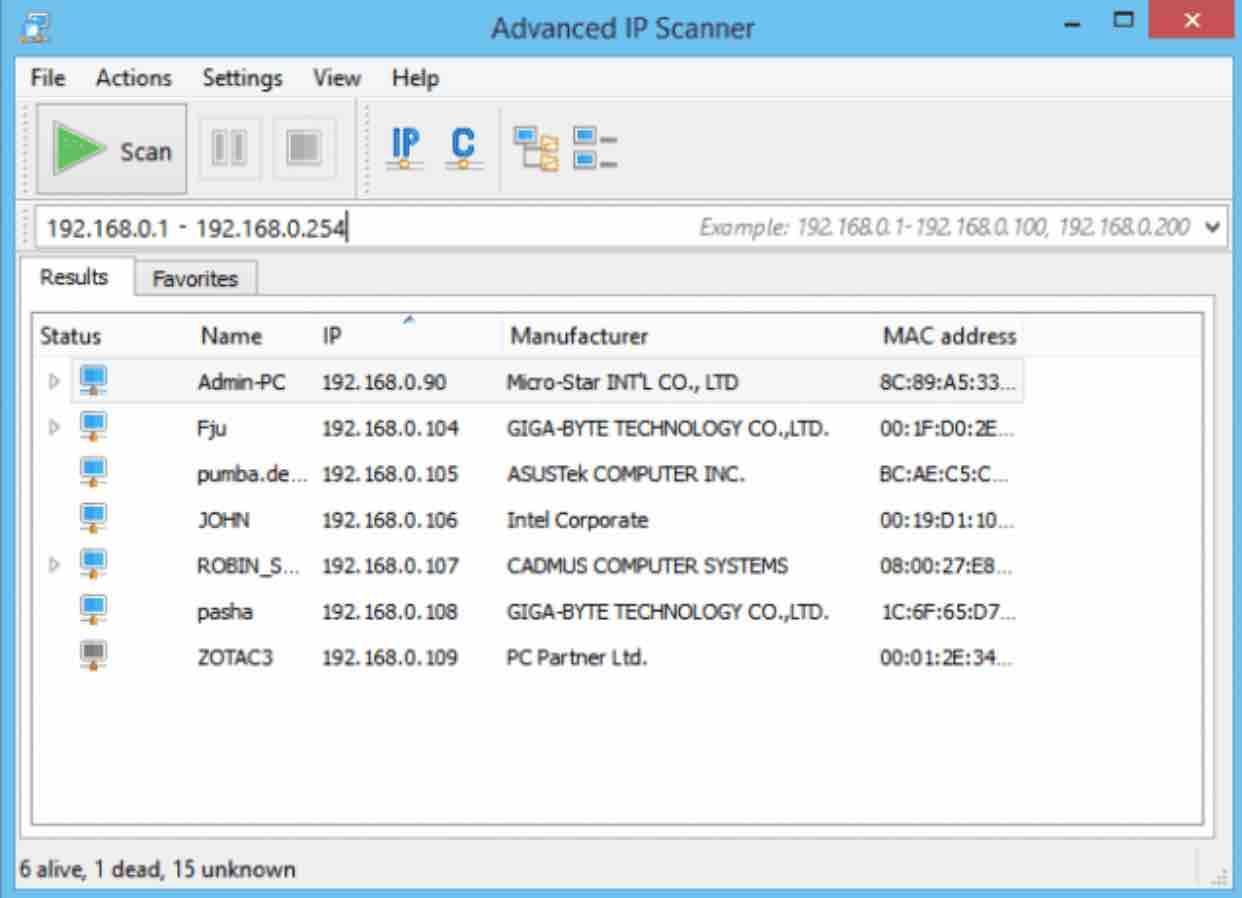
Advanced IP Scanner
It is a network administration tool that can do a number of tasks, such as scanning the network for connections. There are also remote options for Wake-on-LAN and shutdown, connect via HTTP / FTP, as well as remote control with Remote Desktop and Radmin. Of course, it is also useful for a simple network scanner for wireless connections.
By default Advanced IP Scanner will set the address ranges for all connections on the computer, that is, only the range in which WiFi connections are likely to be activated will have to be scanned, such as 192.168.0.1 – 192.168.0.254 . If you only have one active connection, there is no need to touch the IP range.
Read: Securing Your Home’s Digital Frontier: Essential Tips for Preventing Cyber Intrusions
After scanning, all connections will be displayed along with the manufacturer of the wireless device, the MAC address and its name. Advanced IP Scanner does not have to be installed since it has a portable version.
Wireless Network Watcher
Wireless Network Watcher is a NirSoft software . The good news is that it does not require configuring the IP address ranges and automatically starts scanning your primary network adapter showing the connected devices.
Read: How to fix bluetooth problems in Windows 10
Wireless Network Watcher scans the IP range in a few seconds, after which it gets information like IP, Device Name, MAC address, adapter manufacturer, detection amount, and activity status.
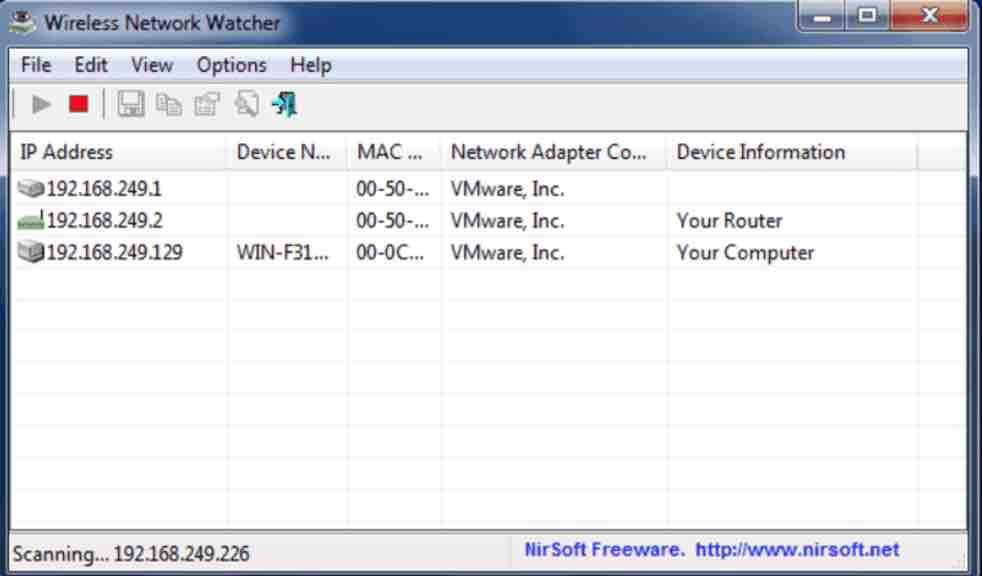
If you want to scan a different adapter or a custom IP address range, use the advanced options by pressing F9. A portable and installer version is available.
SoftPerfect WiFi Guard
SoftPerfect WiFi Guard is like a basic version of the excellent SoftPerfect Network Scanner software . This tool will scan the network for connected devices and re- examine every xx minutes, displaying a message if an unknown connection has been found.
For each connection marked in red that you want to authorize, double-click on it and check the box ” I know this computer or device “, which informs the program to ignore the device during scans.
Read: How to Track A Cell Phone Location Online by Number
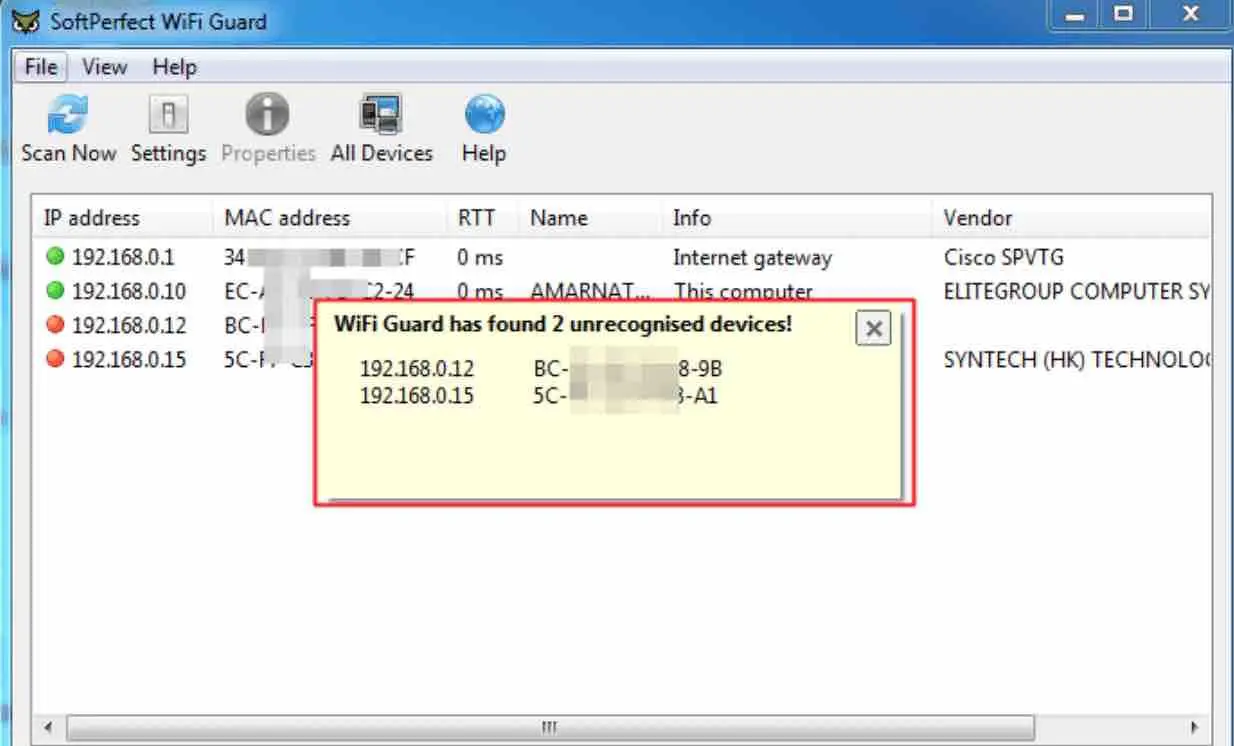
While running or minimized WiFi Guard will scan again between 0 and 60 minutes (default is 30 minutes) and will display a message on the screen if it has detected a new unknown device.
Read: How to fix WiFi not working on Ubuntu
Who Is On My WiFi
This tool is a little different from the others, because its main task is to identify the computers on the network and notify when unknown or unidentified people make a connection to the WiFi network .
Unfortunately, one of its most useful features of blocking unknown or suspicious connections is only available on a paid subscription, plans start slightly at $ 9.95 per month. The free version, however, still allows you to scan and find devices on the network.
The first thing you should do is configure the address range to scan from the default by clicking on the Settings button and enter the range you need for your network (Scan Options), such as 192.168.0.1-254. If you are not sure about going to the diagnostic tab in settings, click “Detect IP ranges” to see what your network is currently using.
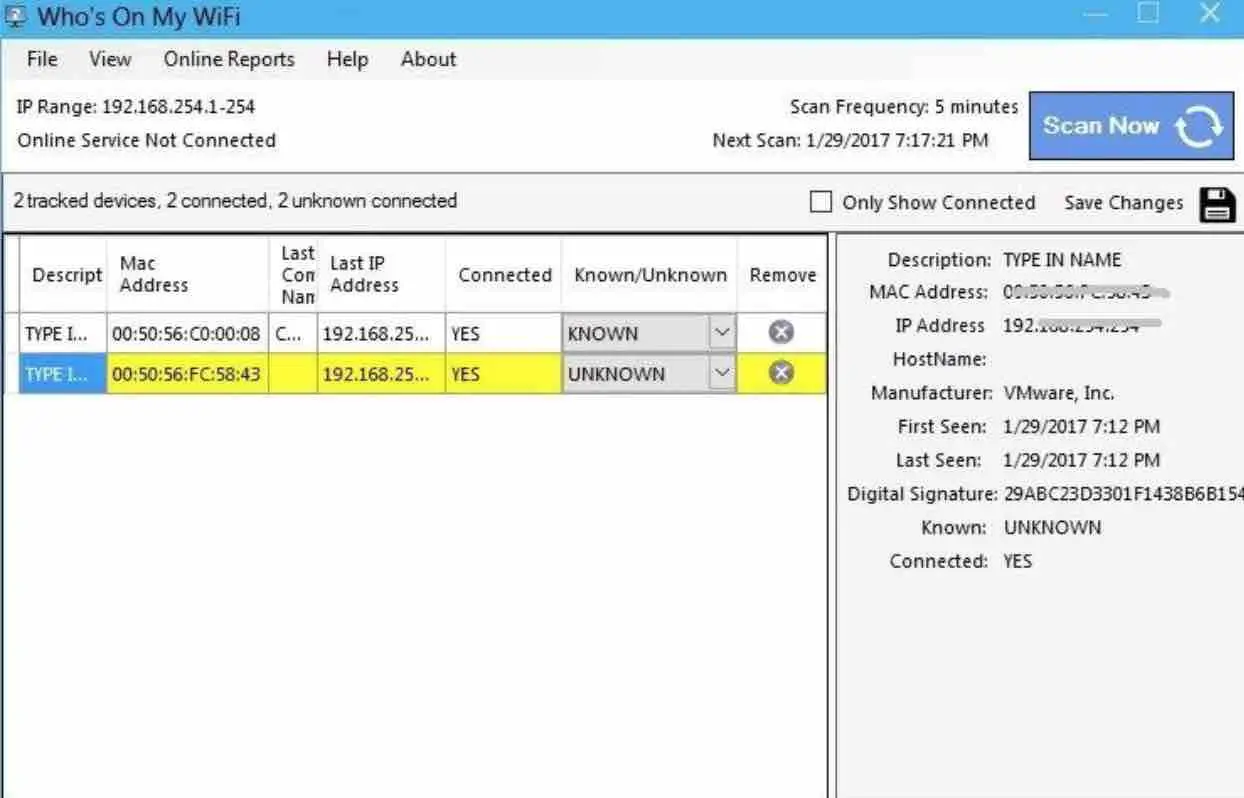
If Who Is On My WiFi is kept running in the background, a visual and audible message will appear when an unknown network device is detected, by default it will be scanned every 5 minutes, although you can change this time from 2 to 10 minutes in the settings .
Read: 15 Proven Ways to Fix Wi-Fi Problems on Your Mac
Be sure to close the Who Is On My WiFi icon in the toolbar if you don’t want to use the monitoring feature.
WiFi Analyzer (iOS, Android)
Available for iOS and Android , the WiFi Analyzer has several options, but focuses on the basics. It is capable of doing a complete analysis and identification of a network, including by manufacturer, all connected devices. With this data, the user can send an alert and even perform a Ping , in order to wait for a response from the receiver.
Such features are necessary to separate your own devices from those of strangers, who cannot be verified personally if they have received the app’s commands. It reveals complete information of each revealed device, such as IP address and MAC address , the latter being very important. The application is free .
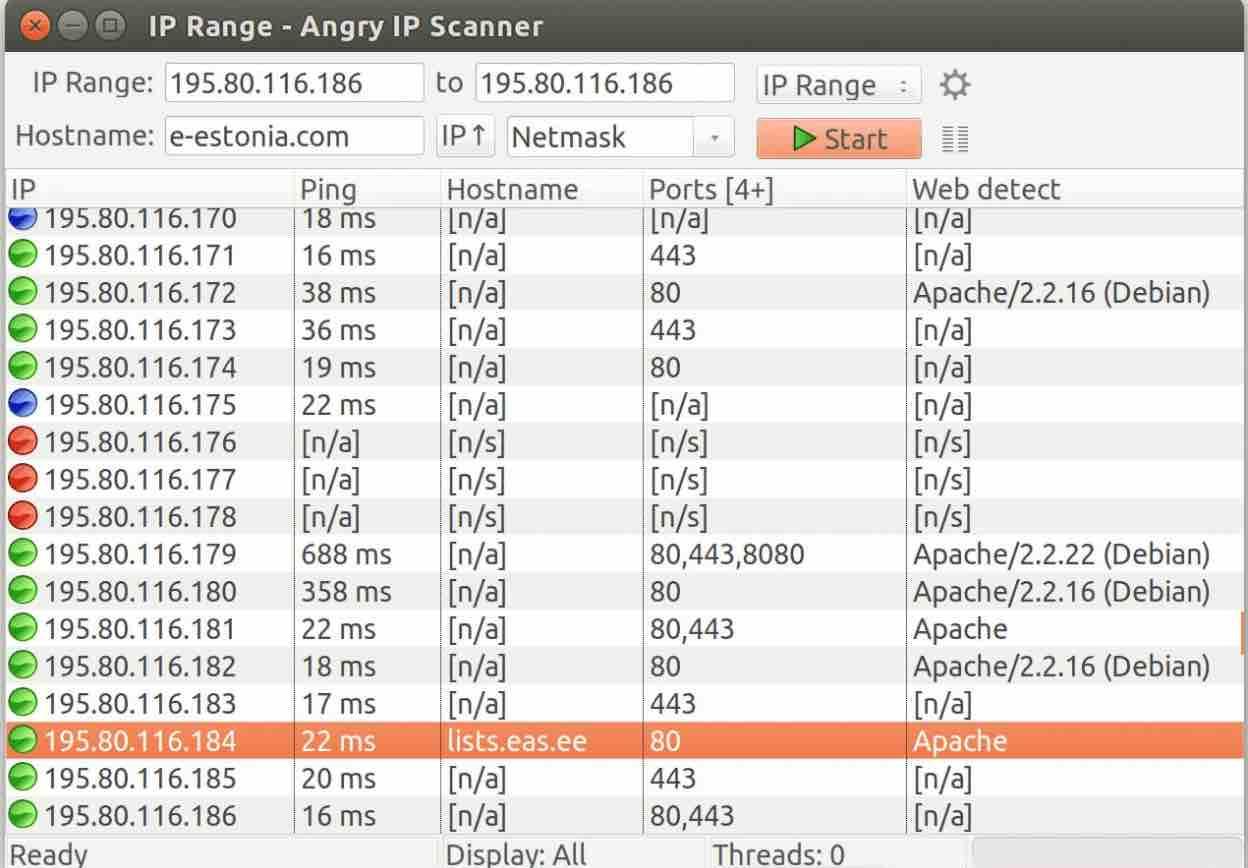
Angry IP Scanner (Windows, macOS and Linux)
Angry IP Scanner is a cross-platform tool that works for Mac and Linux . It is based on Java, which will obviously mean that the Java runtime environment must be installed on your computer.
 Source: Angry IP
Source: Angry IP
You can also reveal the penetrators using your desktop. For this, the Angry IP Scanner program is an excellent choice. It has a simple and even a very great interface, a common feature in open source projects , but it is able to quickly scan the network and identify all connected devices, separating them between active and inactive, in addition to allowing a ping and identification.
Read: Best spy apps for Android phones
The tool simply pings all IP addresses in the selected range for a response and then displays the result along with the information you request in the main window.
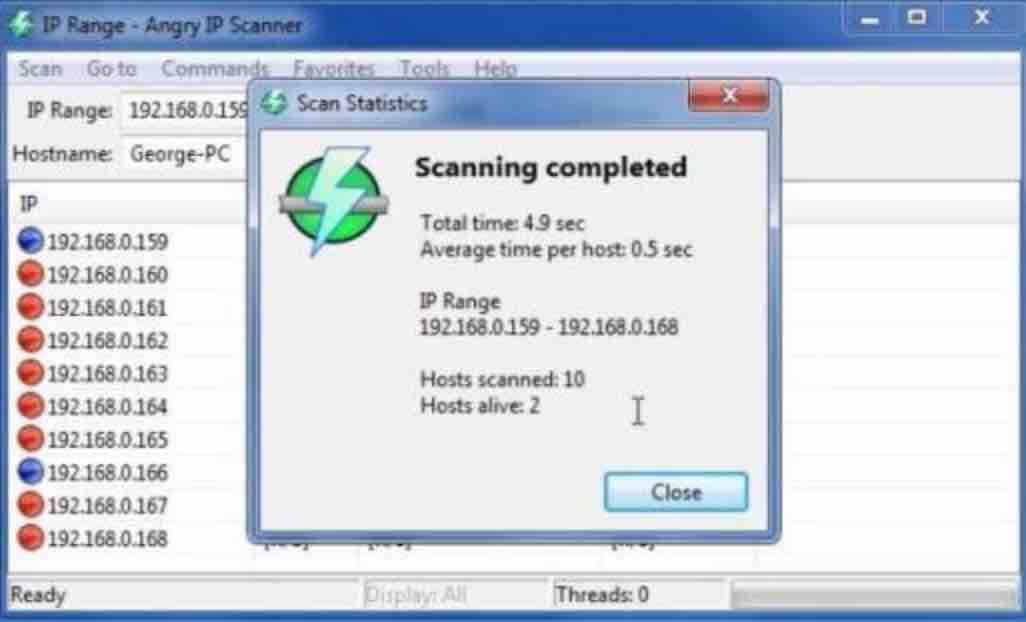
The scanning process is quite fast. To see the result of all the addresses scanned, go to Tools> Preferences> Show and select ” All scanned computers “, this will reveal other connected devices, possibly not responding to the pings. The portable and installation version is available.
Like other mobile applications, it lists the IP and MAC addresses of the connected devices, and because it is free software, Angry IP Scanner is available for both Windows , MacOS and Linux .
Fing application
A very simple way to analyze the network is through the Fing application, which is free and available for iOS and Android .
The Fing is a unique application for Android. It has advanced monitoring and diagnostic tools and has a very intuitive interface for use by laypeople. It allows you to completely scan the Wi-Fi network. The user can send alerts and Ping to track the gadget, in order to separate theirs from those of others. It is also free.
Once the app is downloaded and opened up, you will be able to see, among other things, all the devices connected to the network with their respective IP addresses, manufacturer name and MAC.
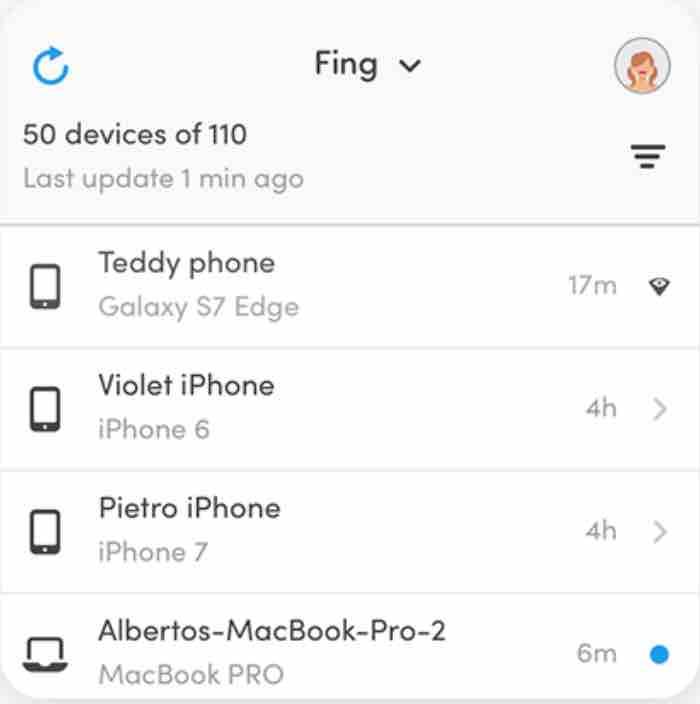
How to see who is connected to my wifi
The MAC address is a unique identifier that every connected device has, from a smartphone, Smart TV or Chromecast to a computer. It is like a unique fingerprint of the computer when communicating with the network.
This data is used to be able to block by MAC or to configure MAC filtering on the router and thus create a white list of devices that are authorized to connect to the network,
Filtering by MAC address
With the Fing app you already have all the MAC addresses. Now you need to enter the router’s control panel and for that you have to do the following:
The internet provider (ISP) may offer users direct access to their router from the company’s web portal. If this is your case, you must contact the company to get access with username and password.
If this option is not available, you can try using the IP address of the router (which is usually written on the base of the router) and write it in the address bar of the browser.
In case the IP address is not found, then the data can be obtained in this way: in Windows, go to the start menu and in the magnifying glass write “cmd”. Immediately a window will show up in which you should type in “ipconfig”.
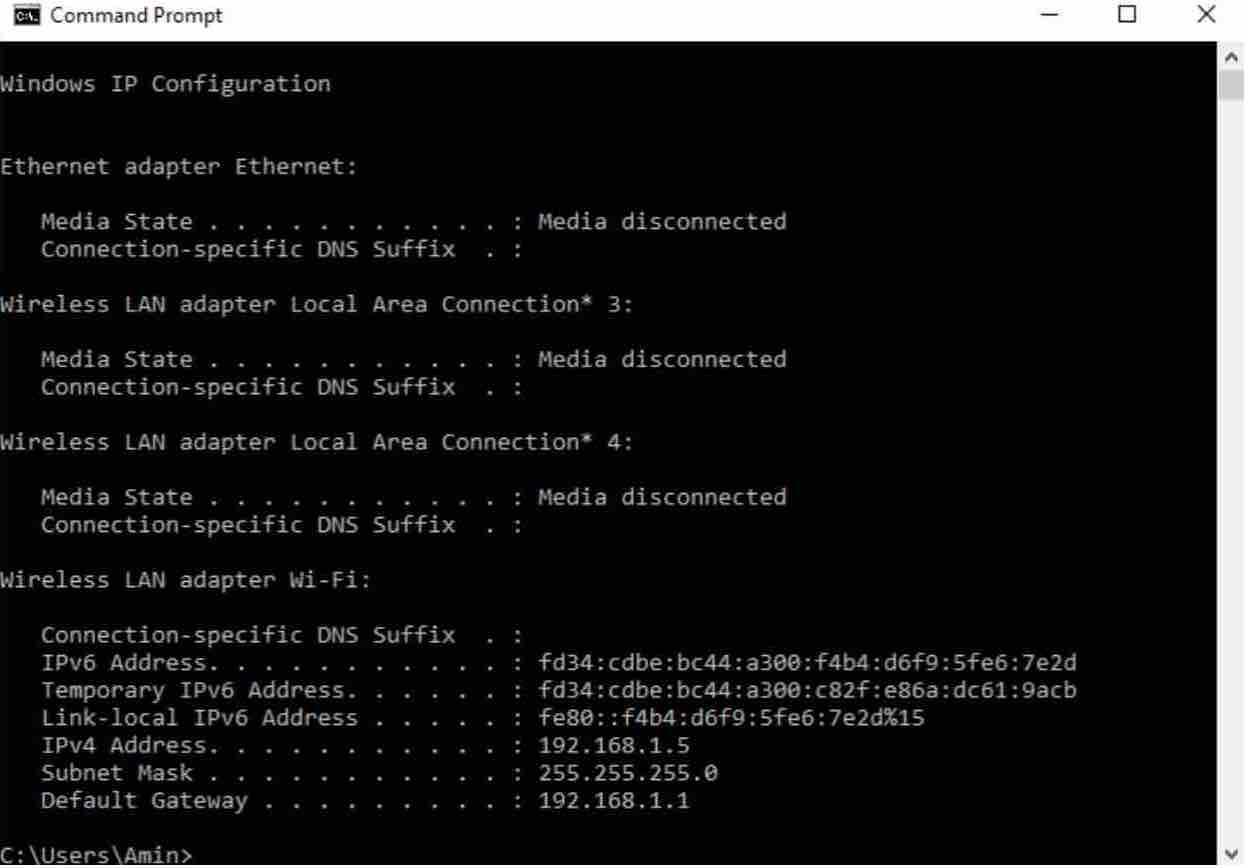
A series of output lines will appear on the screen. The one that is needed is the one that says “Default Gateway” or “Default Gateway”. This is the IP address of the router that must be typed in in the address bar of the browser to access the control panel of the router.
Once there, you must enter the username and password of the home page, which, if not previously modified, is usually “admin” and “1234”, or “admin” in both cases. If that combination does not work, you can find that information in the base of the router or in the manual.
If the option is not found, you can visit www.routerpasswords.com , which has a default key database for various brands and models of routers.
Network Analyzer (iOS)
Source : techet
For iPhone and iPad users, Network Analyzer is a simple and complete app. It allows solving a series of problems related to the network, such as performance and specifications, and provides accurate information about who is connected. It is possible to identify the MAC addresses of gadgets on the network and perform a Ping to identify them, allowing you to know which devices are and which are not. The app is free.
How to ban intrusive devices
The first and simplest thing to do to ban an intruder on your Wi-Fi network is to change your router’s password . Then, in possession of the MAC addresses of all devices you have identified as strangers, it is time to block them directly on your Wi-Fi router (in case they discover the new password or have not been deleted).
To do this, go to the Settings menu and then to Network / Wireless / Wireless Mac Filtering . If the option is disabled, then it is activated.
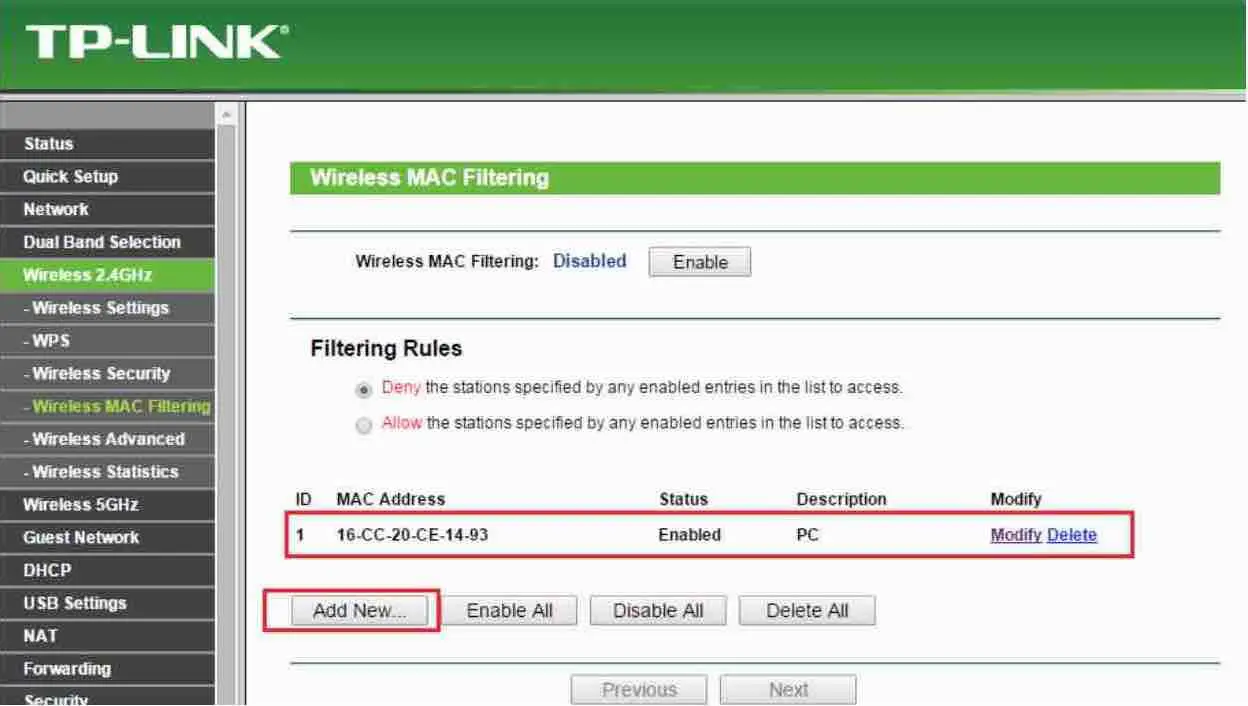
Source: tplink
There, proceed to create a list of MAC addresses authorized to connect, or begin to block “intrusive devices”.
The organization of the router menus varies by manufacturer , but in general everyone has this option; within it, you must include all the MACs of the devices that were listed by the apps, but that you did not recognize as your own; this way, they will be blocked by the router and will no longer be allowed to use your data network, even knowing your network name and password.
Other security measures
Change Password
This option is inside the router’s settings menu, which is accessed by following the steps mentioned above. It is important to generate a robust password, that is, it includes a combination of letters, numbers and symbols. It is suggested, as always, to change the password frequently.
Never use the password that comes standard on your Wi-Fi router . Change to a stronger one, with terms that you can easily identify and memorize. Avoid overly complex passwords, which are not as secure as they look and are difficult to remember.
Encryption
It is convenient to enable WPA2 encryption (and avoid using WEP and WPA), as well as disable Wi-Fi Protected Settings (WPS).
Modify network name or SSID
The name of the network, by default, corresponds to the model or manufacturer and with this information, the attacker already has enough information to exploit a known vulnerability for these routers.
Therefore, it is recommended to modify the name so that, if an attacker wants to enter, he does not have information about the type of router being used (neither manufacturer nor model).
Conclusion
I hope you liked these tools. All of them are very useful to know who is connected to our WiFi network and I invite you to try each one and choose one according to your preferences.
A separate point for Advanced IP Scanner , which is an excellent tool for managing your network and for Who Is On My WiFi , which in its paid version protects your WiFi network by searching, detecting and blocking intruders. Now you can answer the question : who is on my wifi or who is using my wifi .
If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.