If you’re serious about Linux system administration, you need to understand SELinux (Security-Enhanced Linux). It’s not just another security tool;
it’s a fundamental shift in how you control access on your systems. This article dives deep into SELinux. We’ll cover everything from the basic concepts to advanced configuration. Let’s get started!
Why SELinux? Moving Beyond Traditional Security
Disclaimer: Before you apply any of the commands or configurations in this article, please verify that the specific command options and modules are compatible with your current Linux distribution and kernel version. Different distributions or kernel releases may have variations in command syntax and module support, so it’s recommended to test these commands in a safe environment before deploying them in production.
Traditional Linux security relies on Discretionary Access Control (DAC). This means that users “own” their files and processes, and they decide who can access them (read, write, execute). The root user has all the power. This is flexible, but it has major weaknesses:
- Root Compromise: If an attacker gains root access (even briefly), they have complete control of the system. They can change anything, access any file, and run any command.
- User Error: Even a non-malicious user with too much power can accidentally damage the system.
SELinux introduces Mandatory Access Control (MAC). Think of it as a security system built into the kernel itself. It’s not about user permissions anymore; it’s about system-wide policies that define exactly what every process, user, and file can do.
Key Benefits of SELinux:
- Least Privilege: Even the root user is constrained by SELinux policies. A compromised service running as root can’t suddenly access everything.
- Fine-Grained Control: You can define incredibly specific rules. For example, you can allow a web server to access only specific directories and network ports, even if it’s running with root privileges.
- Damage Containment: If an attacker compromises a service, SELinux limits the damage they can do. They can’t “break out” of the confined environment defined for that service.
- Auditing: SELinux logs all access attempts, making it easier to track down security breaches.
Read: A Deep Dive into Linux Operating System Architecture: Components and Functions
Flask Architecture: The Foundation of SELinux
SELinux’s power comes from its underlying architecture, called Flask. It’s a bit like a highly sophisticated security guard for your entire system. Here’s how it works:
Subjects and Objects
- Subjects: Active entities that do things. These are primarily processes (running programs).
- Objects: Passive entities that are acted upon. These include files, directories, network sockets, devices, and even other processes.
Security Contexts
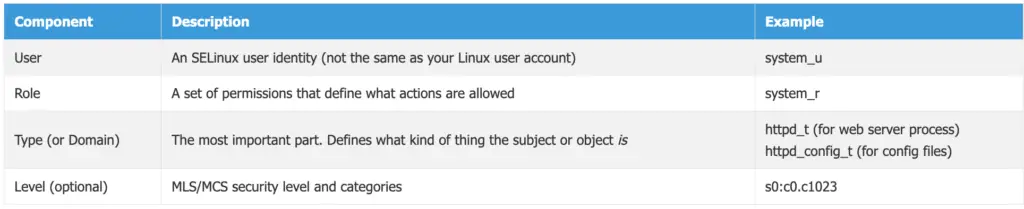
Every subject and object has a security context. This is like a label that describes its security attributes. A security context has three main parts:
- User: An SELinux user identity (not the same as your Linux user account).
- Role: A set of permissions that define what actions are allowed.
- Type (or Domain): The most important part. This defines what kind of thing the subject or object is. For example, a web server process might have a type of
httpd_t, while a web server’s configuration file might have a type ofhttpd_config_t.
Example of a security context: system_u:object_r:httpd_config_t:s0
Read: Securing Your Data: A Practical Guide to Encryption, Integrity, and Signatures in Linux
Policy
The heart of SELinux. The policy is a set of rules that define which subjects can access which objects, and how. For example, a rule might say, “A process with the httpd_t domain can read files with the httpd_config_t type.”
Security Server
This is the part of the kernel that enforces the policy. Every time a subject tries to access an object, the security server checks the policy to see if it’s allowed.
Analogy: Think of a high-security building. People (subjects) have badges (security contexts) with their role (employee, visitor, guard) and clearance level. Rooms (objects) also have labels (security contexts) indicating their security level. The security guards (security server) check the badges against the room labels (policy) to decide who can enter where.
System Administration with SELinux
Traditionally, the root user on a Linux system has unlimited power. SELinux changes that. Even root is subject to the SELinux policy. This is a huge security improvement.
However, it also means you need to be very careful when setting up SELinux. If you get the policy wrong, you can lock yourself out of your own system!
Key Point: Before you enable SELinux in enforcing mode (where it actively blocks unauthorized access), test it thoroughly in permissive mode (where it only logs violations).
Read: Linux Firewall: The Complete Guide to IPtables, NAT, ip6tables and Network Security
Terminology: Understanding the SELinux Language
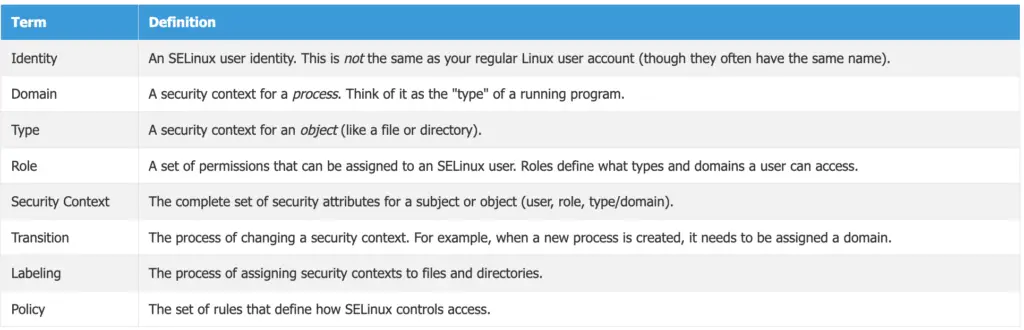
SELinux has its own specialized vocabulary. Here’s a comprehensive glossary:
- Identity: An SELinux user identity. This is not the same as your regular Linux user account (though they often have the same name).
- Domain: A security context for a process. Think of it as the “type” of a running program.
- Type: A security context for an object (like a file or directory).
- Role: A set of permissions that can be assigned to an SELinux user. Roles define what types and domains a user can access.
- Security Context: The complete set of security attributes for a subject or object (user, role, type/domain).
- Transition: The process of changing a security context. For example, when a new process is created, it needs to be assigned a domain.
- Labeling: The process of assigning security contexts to files and directories.
- Policy: The set of rules that define how SELinux controls access.
Read: Linux Shell Deep Dive: Configuring BASH, Managing Jobs, and Optimizing Your Command-Line Workflow
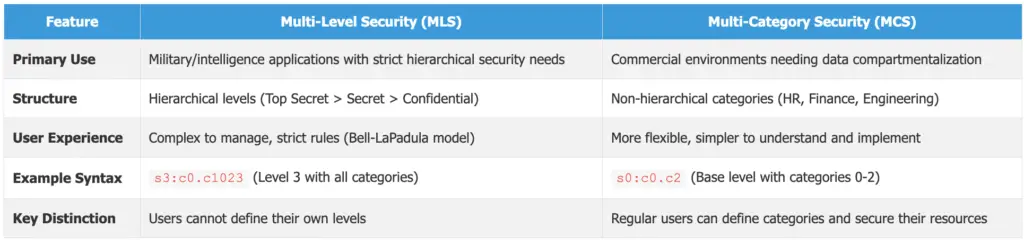
Multi-Level Security (MLS) and Multi-Category Security (MCS)
These are advanced SELinux features that provide even finer-grained control:
Multi-Level Security (MLS)
Adds security levels (like “Top Secret,” “Secret,” “Confidential”). Users and objects are assigned levels, and access is restricted based on those levels. MLS implements a strict hierarchical security model where higher clearance levels can access lower classification levels, but not vice versa.
Multi-Category Security (MCS)
Adds security categories. Think of these like compartments. You can restrict access to objects based on both their level and their category. This is useful for separating different projects or departments.
Important Distinction: MCS, unlike MLS, enables regular users to define categories and secure their resources. MCS is generally more flexible and less complex than MLS, making it more suitable for non-military or intelligence environments.
Read: Secure Your Ubuntu 24.04 System: 30 Essential Steps for Enhanced Security
Basic Management Operations for SELinux
Here are some essential commands for managing SELinux:
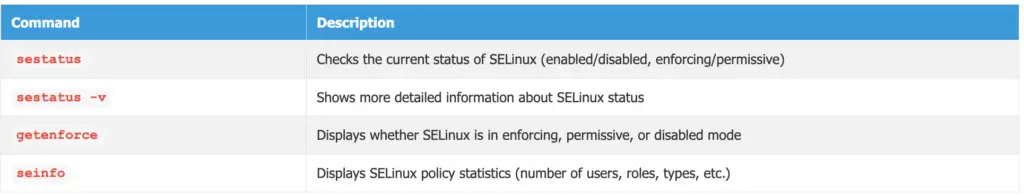
Checking SELinux Status
sestatus: Checks the current status of SELinux (enabled/disabled, enforcing/permissive).sestatus -v # For more detailed informationgetenforce: Displays whether SELinux is in enforcing, permissive, or disabled mode.seinfo: Displays SELinux policy statistics (number of users, roles, types, etc.).
Changing SELinux Mode
setenforce: Temporarily switches between enforcing and permissive mode.# Switch to permissive mode (temporarily)setenforce 0# Switch back to enforcing modesetenforce 1
Checking Security Contexts
id -Z: Shows your current SELinux security context (user, role, type).ps -eZ: Shows the security context of running processes.ls -Z: Shows the security context of files and directories.
Turning Off SELinux
- Temporarily:
setenforce 0 - Permanently: Edit
/etc/selinux/configand change:SELINUX=disabled - At boot: Add
selinux=0to the kernel boot line in your bootloader configuration (usually GRUB).
SELinux Management Tools
Several tools help you manage SELinux effectively:
semanage: A command-line tool for managing SELinux configuration (users, ports, file contexts, etc.). This is the primary tool for most SELinux administration tasks.apol(Security Policy Analysis Tool): A graphical tool for analyzing SELinux policies. Useful for understanding complex policies and visualizing rule interactions.seaudit: A tool for examining SELinux audit logs, helping you identify and diagnose policy violations and security events.audit2allow: A crucial tool that analyzes SELinux denial messages (from the audit log) and generates policy rules to allow the denied access. This is how you fine-tune your SELinux policy in response to legitimate denials.# Example: Generate a policy module from denial logs audit2allow -M mymodule < /var/log/audit/audit.logcheckpolicy: The SELinux policy compiler that converts policy language into a binary format the kernel can use.fixfiles: Corrects file security contexts across the system.restorecon: Restores the default security context for files and directories.# Restore context for the web server directory restorecon -R -v /var/www/htmlchcon: Changes the security context of a file or directory (temporarily).# Change context of a file chcon -t httpd_sys_content_t /path/to/file.html
The SELinux Reference Policy
The SELinux reference policy is a comprehensive, general-purpose SELinux policy. It’s designed to be a starting point for creating your own customized policies. Most distributions (like Red Hat, Fedora, CentOS) use a policy derived from the reference policy (such as the targeted policy).
The reference policy itself is highly modular, organized into logical domains for different system functions and applications. This modular design makes it easier to customize and extend for your specific needs.
Read: How to fix printer issues on Ubuntu 22.04
Policy Methods
SELinux uses several different methods to control access:
- Type Enforcement (TE): The primary method. It focuses on the types of objects (files, directories) and the domains of processes. Rules define which domains can access which types.
- Role-Based Access Control (RBAC): Controls which roles users can assume. Roles are like groups of permissions that determine what domains a user can enter.
- Multi-Level Security (MLS): Adds security levels for environments requiring strict hierarchical access control.
SELinux Users
SELinux has its own concept of users. These are not the same as your regular Linux user accounts. SELinux user identities are used to further refine access control. Common SELinux users include:
system_u: For system processes.user_u: For regular users.root: The SELinux root user (still constrained by policy!).unconfined_u: For users who are minimally constrained by SELinux.
SELinux Configuration Files
SELinux configuration involves working with several important files and directories:
/etc/selinux/config: The main configuration file that controls basic SELinux settings:SELINUX=: Can beenforcing,permissive, ordisabled.SELINUXTYPE=: The type of policy to use (e.g.,targeted,mls).
- Policy Files:
/etc/selinux/[policyname]/policy/policy.[version]: The compiled binary policy file. The version number (e.g., 21) represents the policy format version, which depends on the kernel’s SELinux implementation.
- Development Files:
/usr/share/selinux/devel/: Contains policy development tools and templates for creating custom policies.
- Module Files:
/etc/selinux/[policyname]/modules/: Contains policy modules that can be loaded and unloaded dynamically.policy/modules/admin/: Modules for administrative tasks.policy/modules/apps/: Modules for applications.
- File Context Definitions:
/etc/selinux/[policyname]/contexts/files/file_contexts: Defines the default security contexts for files and directories.
SELinux Policy Rules
Policy rules define how SELinux controls access. They are written in a specific syntax. Here are some of the key rule types:
Type and Role Declarations
Define the types, domains, roles, and users in your system.
type httpd_t;
role system_r types httpd_t;
Access Vector Rules
The most important type of rule. These rules specify which subjects can access which objects, and how. For example:
allow httpd_t httpd_config_t:file { read getattr };
This rule says that a process with the httpd_t domain can read and get attributes of files with the httpd_config_t type.
Type Transitions
Define how processes change domains when executing programs:
type_transition unconfined_t httpd_exec_t:process httpd_t;
This rule says that when a process with domain unconfined_t executes a file with type httpd_exec_t, the resulting process should transition to the httpd_t domain.
Role Allow Rules
Control which roles can transition to other roles:
allow user_r system_r;
This rule allows a user in the user_r role to transition to the system_r role.
File Context Specifications
Define the default security contexts for files and directories:
/var/www/html(/.*)? system_u:object_r:httpd_sys_content_t:s0
This specification assigns the httpd_sys_content_t type to all files in the /var/www/html directory.
Advanced Administrative Operations
Managing File Contexts
semanage fcontext: Manages file context mapping definitions.# Add a new file context definitionsemanage fcontext -a -t httpd_sys_content_t "/custom/web/path(/.*)?"# Apply the new context definitionrestorecon -R -v /custom/web/path
Managing Port Definitions
semanage port: Manages network port type definitions.# Allow the web server to use a non-standard portsemanage port -a -t http_port_t -p tcp 8080
Managing Boolean Settings
SELinux includes “boolean” switches that can easily enable or disable specific policy features:
getsebool: Lists current boolean settings.# List all booleans getsebool -a # Check a specific boolean getsebool httpd_can_network_connectsetsebool: Changes boolean settings.# Enable network connections for the web server setsebool -P httpd_can_network_connect onThe
-Pflag makes the change persistent across reboots.
Troubleshooting SELinux Issues
When SELinux blocks an action, it logs details to the audit log. The most effective way to troubleshoot these issues is:
- Check the audit log for denials:
ausearch -m avc -ts recent - Use
audit2allowto understand the denial and generate a fix:ausearch -m avc -ts recent | audit2allow -a - Create a custom policy module to allow the legitimate action:
ausearch -m avc -ts recent | audit2allow -M myfix semodule -i myfix.pp
Application-Specific Considerations
Different applications have specific SELinux requirements. Here are some common examples:
Web Servers (Apache/Nginx)
Web servers typically run in the httpd_t domain and need access to content with appropriate types:
httpd_sys_content_tfor static contenthttpd_sys_script_exec_tfor scripts (PHP, CGI)httpd_sys_rw_content_tfor writable directories
Boolean settings control additional features:
httpd_can_network_connect_dbfor database connectionshttpd_can_sendmailfor email sending capabilities
Database Servers
Databases typically have their own domains (e.g., mysqld_t for MySQL) and type definitions for data files (e.g., mysqld_db_t).
File Sharing (Samba)
Samba uses the smbd_t domain and needs specific file types and boolean settings to function properly:
samba_share_tfor shared directoriessamba_enable_home_dirsboolean to allow sharing home directories
Conclusion
SELinux provides a powerful layer of security beyond traditional Linux permissions. While it has a learning curve, the protection it offers is well worth the effort to master it. By understanding the core concepts and using the tools outlined in this guide, you can significantly enhance your system’s security posture without compromising functionality.
Remember to start with permissive mode when implementing SELinux, use the troubleshooting tools to diagnose issues, and gradually tighten security as your understanding grows. With practice, SELinux will become an invaluable part of your Linux administration toolkit.
If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.