Picking Ubuntu for your operating system is a solid choice for a secure foundation. But, if you’re serious about safeguarding your system and keeping your important data safe, there are a few extra steps worth taking.
Think of it as adding extra locks to your digital home. This guide is here to walk you through practical, real-world techniques to beef up your Ubuntu security. We’ll touch on essentials like keeping software fresh with security patches, creating passwords that are tough to crack, setting up your firewall correctly, thinking about antivirus options, and a lot more. Follow along with these suggestions, and you’ll significantly strengthen the defenses of your Ubuntu 24.04 setup.
1. Enabling the Ubuntu Firewall (UFW): Your First Defense
Turning on your firewall is a security basic, and thankfully, Ubuntu simplifies this with the Uncomplicated Firewall (UFW). UFW essentially acts as a bouncer for your network traffic, deciding what gets in and what goes out. Consider it your primary shield against unwanted network access.
To get it running, open your terminal and type:
sudo ufw enableJust like that, UFW blocks all incoming connections by default – a strong starting point. However, you’ll need to allow certain traffic for specific services. For instance, if you manage your system remotely using SSH, you’ll need to allow those connections:
sudo ufw allow sshAlternatively, you can specify the port directly (SSH typically uses port 22):
sudo ufw allow 22/tcpRead: How to set up a UFW on Ubuntu 22.04
2. Crafting Strong, Unique Passwords for Better Account Protection
A very common weak spot in security? Easy-to-guess or reused passwords. You can protect yourself from brute-force attacks and other sneaky methods by using strong, unique passwords for every single account. A robust password typically includes:
- Uppercase letters (A-Z)
- Lowercase letters (a-z)
- Numbers (0-9)
- Special symbols (!@#$%^&*)
Steer clear of common dictionary words, personal details (like names or dates), or predictable patterns. Generally, the longer and more complex, the better. I recommend aiming for at least 12 characters, maybe even 16 or more for critical accounts.
Example of a decent structure (but don’t use this exact one!): `Th1sIs@S@mpl3P@ss!`
Read: Linux password generator
3. Keeping Your System Fresh: The Importance of Regular Updates
Making sure your Ubuntu system and all its software are up-to-date is absolutely vital for security. Updates frequently contain critical security patches that close loopholes attackers could exploit. Ubuntu has a handy Software Updater tool, but you can also manage updates via the terminal:
sudo apt update && sudo apt upgradeHere’s what those commands do:
apt update: Fetches the latest list of available software packages and versions from the repositories. It doesn’t install anything yet, just checks what’s new.apt upgrade: Installs the newest versions of all packages already on your system that have updates available.- You might also consider running
sudo apt dist-upgradeoccasionally. It’s smarter about handling dependencies, especially during major system upgrades.
Get into the rhythm of running these commands regularly – maybe once a week – to keep your system patched against the latest threats.
Read: How to fix Ubuntu update errors
4. Setting Up Automatic Security Updates for Hands-Off Protection
For added peace of mind and less manual work, you can tell Ubuntu to install security updates automatically. This keeps your system patched against critical vulnerabilities without you having to remember to do it.
To enable this feature:
- Search for and open the “Software & Updates” application.
- Go to the “Updates” tab.
- Look for the “Automatically check for updates” section. Ensure it’s set to “Daily”.
- Under “When there are security updates:”, select “Download and install automatically”.
You can also configure notifications to stay informed about what’s happening behind the scenes.
Read: Securing Your Data: A Practical Guide to Encryption, Integrity, and Signatures in Linux
5. Using Secure Network Connections (WPA2/WPA3 is Key)
Whenever you connect to a network, especially Wi-Fi, make sure it’s secure. Open, unsecured networks are risky places where others might snoop on your activity. Always choose Wi-Fi networks using WPA2 or, even better, WPA3 encryption. These are the modern standards for wireless security. Avoid older protocols like WEP – they’re easily cracked. If you manage your own router, double-check that it’s set to WPA3 or at least WPA2-AES.
Read: How to resolve WiFi Issues on Ubuntu 24.04
6. Being Smart About Installing New Software
Stick to installing software from sources you trust. The official Ubuntu repositories (accessed via the Software Center or `apt`) are your safest bet, as the software there is vetted. Reputable third-party sources known for their reliability are generally okay too. Be very cautious about downloading software from unknown or random websites – they might bundle malware. A quick search about the software source before installing can save you trouble. For extra caution with untrusted software, consider testing it in a virtual machine first.
To install software from the official repositories (like the VLC media player), use:
sudo apt install vlcRead: How to download YouTube videos with VLC Media Player
7. Considering Antivirus Software for an Extra Security Layer
While Linux systems like Ubuntu generally see less malware than other platforms, using an antivirus scanner can add another layer of protection. This is particularly relevant if you often exchange files with Windows or macOS systems. Options for Ubuntu include the open-source ClamAV or commercial solutions like Sophos.
To install ClamAV:
sudo apt install clamav clamav-daemonKeep its virus definitions current:
sudo freshclamYou can then scan directories, like your home folder:
clamscan -r /homeThe -r flag tells it to scan recursively (including subfolders). Setting up scheduled scans using `cron` is a good practice.
Read: Linux Storage Mastery: Complete Guide to RAID and LVM Configuration for System Administrators
8. Enabling Full Disk Encryption (FDE) to Protect Data at Rest
Full Disk Encryption (FDE) is a powerful way to protect your data if your laptop or computer is lost or stolen. It scrambles the entire contents of your hard drive, making it unreadable without the correct password or key. Ubuntu uses LUKS (Linux Unified Key Setup) for this. The easiest way to enable FDE is during the Ubuntu installation process. Doing it later is possible but much more involved and carries risks if not done correctly – always back up your data first!
Read: How to make Raspberry Pi safer
Encrypting a disk *after* installation typically involves partitioning, formatting with LUKS, opening the encrypted volume, creating a filesystem, and mounting it. Here’s a very simplified example for a *separate* disk (`/dev/sdb`). **Warning: This is illustrative; follow detailed guides and back up data before attempting this on your system.**
- Format with LUKS: (This erases the target disk!)
sudo cryptsetup luksFormat /dev/sdb - Open the encrypted volume:
sudo cryptsetup luksOpen /dev/sdb my_encrypted_volume(This creates `/dev/mapper/my_encrypted_volume`)
- Create a filesystem:
sudo mkfs.ext4 /dev/mapper/my_encrypted_volume - Mount it:
sudo mount /dev/mapper/my_encrypted_volume /mnt/secure_data(Assuming `/mnt/secure_data` exists)
Read: Moving the Home folder to another partition in Ubuntu
9. Implementing a Screen Lock for Physical Security
This one’s simple but effective: always lock your screen when you step away from your computer. It prevents anyone nearby from accessing your session. You can find the settings for this in:
Settings > Privacy & Security > Screen Lock (Path might vary slightly by Ubuntu version/desktop environment)
Make sure you use a strong password or PIN for the lock, and set it to lock automatically after a short period of inactivity.
Read: Linux Shell Deep Dive: Configuring BASH, Managing Jobs, and Optimizing Your Command-Line Workflow
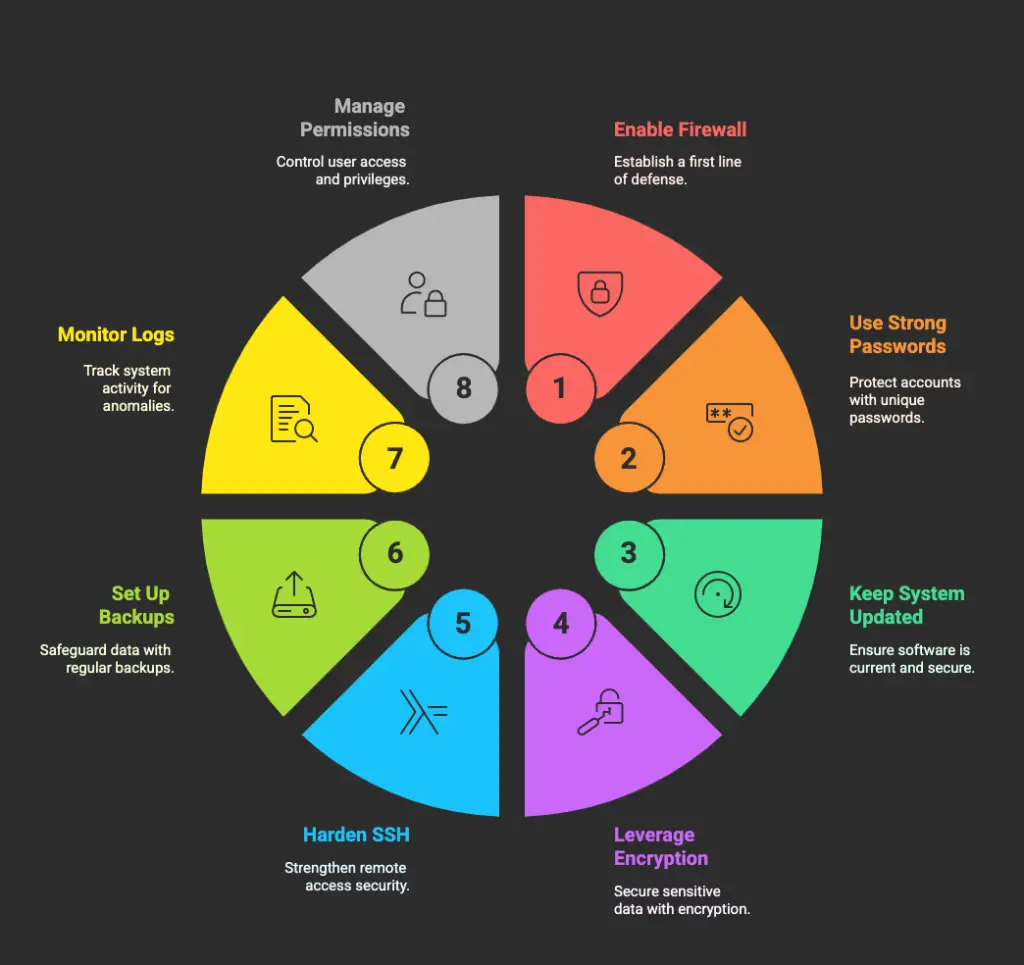
Ubuntu security practicies
10. Using Two-Factor Authentication (2FA) for Stronger Account Logins
Two-Factor Authentication (2FA) adds a crucial security layer to your online accounts. Besides your password, it asks for a second proof of identity, like:
- Something you have: A code from an authenticator app (like Google Authenticator, Authy) or sent via SMS, or a physical security key.
- Something you are: A fingerprint or facial scan (less common for Linux logins, more for online services).
Tools like `oathtool` can be used on the command line for generating time-based codes (TOTP):
sudo apt install oathtoolEnable 2FA wherever possible – for your email, cloud storage, banking, social media, etc. It makes it much harder for someone to get into your accounts even if they steal your password.
Read: Unlock Advanced Linux Security with SELinux: The Ultimate Guide to Access Control and Hardening
11. Limiting System Access with Separate User Accounts
If multiple people use the same computer, give each person their own user account. This isn’t just about tidiness; it’s good security practice:
- Accountability: Easier to see who did what.
- Privacy: Keeps personal files and settings separate.
- Containment: If one account gets compromised, the others are usually less affected.
Manage user accounts easily through:
Settings > Users
12. Enabling AppArmor for Application-Level Security
AppArmor is a security module built into Ubuntu that restricts what programs are allowed to do. It confines applications to a specific set of resources and actions, helping to prevent a compromised application from damaging your system or accessing sensitive files it shouldn’t. AppArmor is typically enabled by default for many core applications.
To work with AppArmor:
- Install utilities (if needed):
sudo apt install apparmor-utils - Check Status: Ensure it’s active.
sudo systemctl status apparmorOr check loaded profiles:
sudo apparmor_status
AppArmor uses profiles (usually stored in `/etc/apparmor.d/`) to define these restrictions.
Read: 4 Ways to Find Large Files on Linux and Free Up Disk Space
13. Using a VPN for Secure and Private Internet Browsing
A Virtual Private Network (VPN) encrypts your internet connection and routes it through a server operated by the VPN provider. This hides your real IP address and encrypts your traffic, making it much safer to use public Wi-Fi and enhancing your online privacy. Choose a reputable VPN provider, ideally one with a strict no-logs policy.
Common VPN protocols/clients used on Ubuntu:
- OpenVPN: A widely supported, robust open-source option.
- WireGuard: A newer protocol known for speed and simplicity.
- Many commercial VPN providers (like ProtonVPN, Mullvad, NordVPN, etc.) offer dedicated Linux clients or configuration files for OpenVPN/WireGuard.
You’ll typically subscribe to a service and then install their client or configure NetworkManager.
Read: Top 11 Linux Log Monitoring Tools for System Administrators
14. Prioritizing HTTPS for Secure Web Connections
HTTPS (the ‘S’ stands for Secure) encrypts the data exchanged between your browser and the websites you visit. Always look for the padlock icon in your browser’s address bar – this indicates a secure HTTPS connection. Most modern browsers will warn you about unencrypted HTTP sites. Make it a habit to ensure you’re using HTTPS, especially when logging in or entering sensitive information. Browser extensions like “HTTPS Everywhere” (though becoming less necessary as sites adopt HTTPS) can help enforce this.
Read: HTTP or HTTPS: What’s the Difference and Which One is Better to Use
15. Implementing Key-Based Authentication and Hardening SSH
If you use SSH (Secure Shell) for remote connections, switching from passwords to key-based authentication drastically improves security. You generate a pair of cryptographic keys: a private key (keep it secret on your computer!) and a public key (copy it to the server). This eliminates the risk of password guessing (brute-force) attacks. **Crucially, disable password authentication after setting up keys.**
Here’s the basic process:
- Generate Keys on Your Local Machine: (Use a strong passphrase!)
ssh-keygen -t rsa -b 4096(This creates `~/.ssh/id_rsa` (private) and `~/.ssh/id_rsa.pub` (public))
- Copy Public Key to the Server: (Replace `user` and `remote_host`)
ssh-copy-id user@remote_host - Disable Password Login on the Server (Highly Recommended):
Edit the SSH server configuration file:sudo nano /etc/ssh/sshd_configMake sure these lines are set (or add them):
PasswordAuthentication no PermitRootLogin no ChallengeResponseAuthentication noRestart the SSH service:
sudo systemctl restart sshd(Or `sudo systemctl restart ssh` depending on the system)
**Test your key login in a *new* terminal window *before* closing the current one!**
Read: How to use scp command in Linux to transfer files securely using ssh
16. Enabling System Auditing (`auditd`) for Deeper Monitoring
System auditing lets you log detailed information about events happening on your system – logins, file access attempts, commands run, etc. This log can be invaluable for security analysis and incident investigation. Ubuntu uses the `auditd` framework for this.
To get started:
- Install the audit package:
sudo apt install auditd - Enable and start the service:
sudo systemctl enable auditd sudo systemctl start auditd
Audit rules, which define what gets logged, are configured in `/etc/audit/rules.d/`. Analyzing the logs is typically done using `ausearch` and `aureport` commands. Setting up useful audit rules requires some understanding of system events.
17. Considering SELinux for Advanced Mandatory Access Control
SELinux (Security-Enhanced Linux) is another Mandatory Access Control (MAC) system, like AppArmor, but generally considered more comprehensive and granular (and also more complex to manage). It uses labels on files and processes to enforce highly detailed security policies. While AppArmor is the default in Ubuntu, SELinux is available and often favored in environments needing very strict security controls (like RHEL-based systems).
Using SELinux on Ubuntu involves:
- Installing SELinux packages:
sudo apt install selinux-basics selinux-policy-default auditd(auditd is often needed)
- Activating SELinux: (Requires a reboot)
sudo selinux-activate
Configuring SELinux policies (defining what’s allowed) is a significant undertaking and requires careful study.

Read: How to Configure Network Settings in Ubuntu 22.04
18. Choosing a Security-Minded Web Browser
While standard browsers like Firefox and Chromium (base for Chrome) have solid security features, some browsers go the extra mile for privacy and security. The Tor Browser routes your traffic through the anonymizing Tor network. Brave Browser includes built-in blocking of ads and trackers.
To easily install the Tor Browser on Ubuntu:
sudo apt install torbrowser-launcherRunning this launcher will download and keep the actual Tor Browser updated for you.
19. Encrypting Your Communications for Enhanced Privacy
Protecting your emails and messages from prying eyes requires encryption. Several tools can help with this on Ubuntu:
- GnuPG (GPG): The standard for email encryption (PGP). Often used with email clients like Thunderbird via extensions (formerly Enigmail, now integrated). Generate keys with `gpg –gen-key`.
- OpenSSL: A powerful command-line toolkit for various cryptographic tasks, including file encryption.
- Secure Messaging Apps: Tools like Signal provide end-to-end encrypted messaging (see section 24).
Read: How to encrypt a USB stick on Ubuntu
20. Using a Password Manager: Your Secure Digital Vault
Trying to remember dozens of strong, unique passwords is impossible. A password manager is the solution. It securely stores your passwords in an encrypted database and can help you generate strong ones.
Good options available on Ubuntu:
- KeePassXC: A popular open-source, offline password manager.
sudo apt install keepassxc - Bitwarden: An excellent open-source option with cloud sync and clients for all platforms (including a desktop app for Linux). Often installed via Snap or Flatpak.
- Pass: A simple, command-line based manager using GPG.
sudo apt install pass - LastPass: Commercial option with a command-line interface available.
21. Selecting a Security-Aware Email Client
If email privacy is a top concern, choose a client that supports robust security features:
- Thunderbird: A well-regarded, open-source client with built-in support for OpenPGP encryption (integrating functionality previously provided by the Enigmail extension).
sudo apt install thunderbird - ProtonMail Bridge: If you use ProtonMail’s encrypted service, this tool lets you use standard clients like Thunderbird while maintaining end-to-end encryption.
Read: How to Install and Remove Software on Ubuntu
22. Exploring Secure File Management Options
Some tools offer extra security for your files, like easy encryption:
- Built-in Archive Manager: Often allows creating password-protected archives (like .zip or .7z).
- VeraCrypt: Powerful open-source tool for creating encrypted volumes (files or partitions), successor to TrueCrypt. Available for Linux.
- Cryptomator: Focuses on encrypting files transparently before they sync to cloud storage.
sudo apt install cryptomator(May need adding a PPA or using Flatpak/Snap)
- Gnome Encfs Manager (Older): GUI tool for managing EncFS encrypted folders. (EncFS has known security critiques, use with caution).
sudo apt install gnome-encfs-manager
23. Opting for Privacy-Respecting Search Engines
Mainstream search engines often track your searches to profile you for advertising. If you prefer more privacy, try these alternatives:
- DuckDuckGo: Popular choice that doesn’t track your search history.
- StartPage: Provides Google search results but anonymizes your query first.
- SearXNG: A free, open-source metasearch engine you can self-host or use public instances of, aggregating results privately.
- Brave Search: From the makers of the Brave browser, focused on privacy.
24. Using Secure Messaging Apps with End-to-End Encryption
For private conversations, use messaging apps that encrypt messages end-to-end (E2EE). This ensures only you and the intended recipient(s) can read them.
- Signal: Widely recommended for its strong E2EE and focus on privacy. Has a Linux desktop client.
- Wire: Another E2EE option, popular in some business contexts.
- Element: A decentralized E2EE messenger based on the Matrix protocol.
- WhatsApp: Uses the Signal protocol for E2EE, but owned by Meta (Facebook), raising privacy concerns for some.
25. Considering Privacy-Focused Cloud Storage Solutions
If you store files in the cloud, consider providers prioritizing security and privacy, especially those offering “zero-knowledge” encryption (where even the provider can’t access your decrypted files).
- Nextcloud: Open-source software you can self-host, giving you full control over your data and cloud features.
- Tresorit: Commercial service known for strong E2EE and security features.
- Proton Drive: E2EE cloud storage from the creators of ProtonMail.
- Sync.com: Another commercial provider focused on E2EE.
- Cryptomator (Client-side): Can be used with *any* cloud provider (Dropbox, Google Drive etc.) to encrypt files *before* they are uploaded.
26. Implementing Enhanced Backup Strategies (The 3-2-1 Rule)
Good backups are non-negotiable. They’re your safety net against hardware failure, accidental deletions, or ransomware. A solid approach is the 3-2-1 rule:
- 3 Copies: Keep at least three copies of your important data (your live data plus two backups).
- 2 Different Media: Store these copies on at least two different storage types (e.g., internal drive, external USB drive, network storage, cloud).
- 1 Offsite Copy: Ensure at least one backup copy is physically located elsewhere (e.g., cloud storage, a drive stored at a friend’s house) to protect against local disasters like fire or theft.
Helpful backup tools on Ubuntu:
- Deja Dup (Backups): Ubuntu’s default user-friendly backup tool, often integrates well with the desktop.
- Timeshift: Excellent for creating system snapshots – great for rolling back system changes, less so for personal data.
sudo apt install timeshift - rsync: Powerful command-line utility for file synchronization, forms the basis of many backup scripts.
- BorgBackup: Feature-rich command-line tool offering deduplication (saves space) and encryption.
sudo apt install borgbackup - Rclone: Command-line tool for syncing files with numerous cloud storage providers.
Remember to automate your backups (using `cron` or systemd timers) and periodically test restoring files to ensure the backups work! Encrypt backups containing sensitive data.
27. Exploring Advanced Threat Detection (IDS/IPS)
Intrusion Detection Systems (IDS) monitor for suspicious activity, while Intrusion Prevention Systems (IPS) can also take action to block threats.
- Fail2ban: Monitors log files for patterns like repeated failed login attempts and automatically blocks the offending IP addresses using the firewall (UFW). Highly recommended for servers.
sudo apt install fail2banConfiguration happens in `/etc/fail2ban/`. Start by creating a `jail.local` file to override defaults.
- OSSEC / Wazuh: More comprehensive Host-based Intrusion Detection Systems (HIDS) that perform log analysis, file integrity checking, rootkit detection, and more. More complex setup.
- Snort / Suricata: Network Intrusion Detection/Prevention Systems (NIDS/NIPS) that analyze network traffic for malicious patterns. Usually deployed on a gateway or dedicated machine.
sudo apt install snortor
sudo apt install suricata
28. Managing User Privileges Wisely (Principle of Least Privilege)
This is a fundamental security concept: grant users and processes only the minimum permissions needed to do their job. Avoid using the root account for daily tasks.
- Use `sudo`: Execute administrative commands with `sudo` only when necessary, instead of logging in as root.
- Separate Accounts: Use non-administrative accounts for regular work.
- File Permissions: Use standard Linux permissions (owner/group/other) correctly. Avoid overly permissive settings like `chmod 777`. Understand group memberships.
- Review `sudoers`: Be careful about who has `sudo` access. Edit the configuration safely using `sudo visudo`. You can restrict which commands specific users can run via `sudo`.
29. Effective Monitoring and Log Management Practices
Keep an eye on your system by regularly reviewing logs for unusual or suspicious activity.
- Key System Logs: Found in `/var/log/`:
syslogormessages: General system activity.auth.log: Login attempts, `sudo` usage, authentication events.kern.log: Kernel messages.ufw.log: Firewall activity (if logging enabled).- Application-specific logs (e.g., `/var/log/apache2/`, `/var/log/nginx/`).
- Log Viewing Tools:
journalctl: Query the systemd journal (modern standard).less,tail,grep,awk: Classic command-line tools for viewing and searching text log files.
- Log Rotation: Use `logrotate` (configured in `/etc/logrotate.conf` and `/etc/logrotate.d/`) to manage log file size and prevent disks from filling up.
- Centralized Logging (Advanced): In multi-server environments, tools like Graylog, Splunk, or the ELK/EFK stack can aggregate logs for easier analysis.
Read: How to Troubleshoot and Optimize Ubuntu Startup: Manage Systemd Services for Faster Boot Time
30. Securing Containers and Virtualization Environments
If you’re using technologies like Docker, LXC, KVM, or VirtualBox, remember they have their own security considerations:
- Containers (e.g., Docker):
- Use minimal, official base images from trusted sources.
- Keep images updated; rebuild frequently.
- Run container processes as a non-root user whenever possible (use the `USER` directive in Dockerfiles).
- Limit container resource usage (CPU, memory).
- Scan images for vulnerabilities using tools like Trivy or Clair.
- Leverage security features like AppArmor/SELinux profiles for containers.
- Don’t mount sensitive host directories into containers unnecessarily.
- Virtual Machines (e.g., KVM, VirtualBox):
- Keep the host OS and virtualization software patched.
- Apply security best practices *inside* the guest VMs (updates, firewall, etc.).
- Isolate VM network traffic using virtual networks if needed.
- Use strong passwords/keys for VM access.
- Keep VM snapshots tidy and manage VM backups.
Read: How to install and setup Docker on Ubuntu 22.04
Frequently Asked Questions (FAQ) about Ubuntu Security
1. Is Ubuntu secure right after installation?
Ubuntu has a good security foundation (user permissions, frequent updates, AppArmor), making it generally more secure out-of-the-box than some alternatives. However, it’s not perfectly secure by default. You still absolutely need to take steps like enabling the UFW firewall (it’s installed but inactive), consistently applying updates, and using strong passwords to establish a basic level of security.
2. Do I truly need antivirus software on my Ubuntu desktop?
The risk of traditional viruses targeting Linux desktops is lower than on Windows, but it’s not non-existent. Antivirus (like ClamAV) is more strongly recommended if you:
- Frequently download files from less trusted websites or sources.
- Exchange files often with Windows/macOS users (to avoid passing malware along).
- Run publicly accessible services (like a web server or mail server).
- Simply want an additional layer of security for peace of mind.
For careful desktop users sticking mainly to official software sources, the risk is lower, but scanning occasionally can still be a good idea.
3. What’s the practical difference between `apt update` and `apt upgrade`?
Think of it this way: `sudo apt update` is like checking the menu at a restaurant – it finds out what dishes (packages) are available and what the latest versions are. It doesn’t bring you any food. `sudo apt upgrade` is like ordering the updated versions of the dishes you already have at your table. It downloads and installs the newer versions of packages currently installed on your system. You *always* need to run `update` before `upgrade` so that `upgrade` knows what the latest versions are.
4. Can you explain the difference between AppArmor and SELinux simply?
Both AppArmor and SELinux are security systems (Mandatory Access Control or MAC) designed to limit what programs can do, adding security beyond basic file permissions.
- AppArmor: It’s generally seen as simpler to learn and manage. It works by defining rules based on file paths (e.g., “this program can only read files in `/var/www`”). It’s the default MAC system in Ubuntu.
- SELinux: It’s more powerful and offers finer control but has a much steeper learning curve. It assigns security labels to everything (files, processes) and writes complex policies about how labeled items can interact. It’s common in Red Hat-based systems and high-security environments.
For most Ubuntu users, AppArmor provides a significant security boost without the complexity of SELinux.
5. Why is disabling password authentication for SSH so important?
Password logins for SSH are a prime target for automated “brute-force” attacks, where bots try thousands of common passwords per minute. SSH keys are far more secure. They use cryptography – you have a private key (kept secret) and a public key (on the server). Logging in requires proving you possess the private key, which is computationally infeasible for an attacker to guess or forge. By disabling password authentication entirely (`PasswordAuthentication no` in `sshd_config`), you eliminate the entire category of password-guessing attacks against your SSH server.
6. What does the “principle of least privilege” mean in practice on Ubuntu?
It means giving any user or process only the bare minimum permissions necessary to perform its function, and nothing more. In practice on Ubuntu, this means:
- Don’t use the `root` account for everyday tasks. Use your regular user account.
- Use `sudo` only for specific commands that require administrative rights.
- Don’t give applications more permissions than they need (e.g., don’t run your browser as root).
- Configure file permissions carefully – avoid `chmod 777`.
- Limit who can use `sudo` in the `/etc/sudoers` file.
This limits the potential damage if an account or application is compromised.
7. How frequently should I perform backups on my Ubuntu system?
This depends on how critical your data is and how often it changes. A good rule of thumb:
- Critical Data (work documents, code, databases): Daily backups are often recommended, perhaps even more frequently for very active data.
- Personal Files (photos, general documents): Weekly might be sufficient if they don’t change constantly.
- System Configuration: Backup before and after major system changes. Tools like Timeshift are great for system state snapshots.
The most important thing is to have a *regular, automated* backup schedule and to *test your restores* periodically.
8. What defines a “zero-knowledge” cloud storage service?
A zero-knowledge provider uses end-to-end encryption where the encryption and decryption happen *only* on your device (client-side). You hold the encryption keys, not the provider. This means the provider has “zero knowledge” of the contents of your files stored on their servers. Even if legally compelled or hacked, they cannot hand over readable data because they don’t have the keys to decrypt it.
9. This is a lot of information! Where’s the best place to start securing Ubuntu?
Don’t feel overwhelmed! Focus on the fundamentals first. I’d recommend starting with these high-impact steps:
- Enable UFW Firewall: `sudo ufw enable`. Simple, crucial first step.
- Use Strong, Unique Passwords: For your user login and all online accounts. Get a password manager to help.
- Update Regularly: Run `sudo apt update && sudo apt upgrade` weekly, or enable automatic security updates.
- Use HTTPS: Be mindful of the padlock in your browser.
- Install Software Carefully: Stick to official repositories (Software Center, `apt`) or trusted sources.
Mastering these basics provides a massive security improvement. You can then explore other steps like SSH keys, backups, and 2FA as you get more comfortable.
10. What are common signs that my Ubuntu system might be compromised?
Detecting a compromise can be tricky, but watch out for:
- Sudden Performance Issues: Unexplained slowness, high CPU/network usage.
- Strange Network Activity: Data usage spikes, connections to unknown servers (tools like `netstat` or `ss` can help).
- Unfamiliar Files or Processes: New files appearing (especially in system areas), processes running that you don’t recognize (`top`, `htop`).
- Changed System Settings: Firewall rules altered, new users added, services enabled/disabled without your action.
- Odd Behavior: Files modified or deleted, strange pop-ups (rare on desktop Linux), login failures you didn’t cause.
- Antivirus Alerts: If you run AV software and it flags something.
- Account Lockouts/Alerts: Emails about login attempts or password changes for your online accounts originating from your system’s IP.
- Log Anomalies: Unusual errors or repeated login failures in `/var/log/auth.log` or other logs.
If you suspect a compromise, the safest steps are usually to disconnect the machine from the network immediately, back up critical data (carefully, as backups could be tainted), and plan for a full system reinstall from trusted media. Investigating thoroughly often requires expertise.
Conclusion
Securing your Ubuntu machine isn’t a one-off checklist; it’s more like an ongoing habit. By consistently applying the practices we’ve covered – like enabling the firewall, using strong passwords and a manager, keeping everything updated, leveraging encryption where needed, hardening SSH, setting up solid backups, monitoring logs, and being mindful of permissions – you build multiple layers of defense. No single technique is perfect, but together they significantly raise the bar against potential threats, protecting your valuable data and giving you peace of mind. Take the time to implement these steps; it’s a worthwhile investment in your digital security on the excellent Ubuntu platform.
If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.