As Linux administrators, securing our systems and networks is one of our most critical responsibilities. Firewalls serve as the cornerstone of that security, and in the Linux ecosystem, iptables, ip6tables,
and Network Address Translation (NAT) are your primary defensive tools. This guide provides practical, hands-on instructions for understanding and configuring these powerful firewall components.
Disclaimer: Before applying any commands or configurations from this guide, verify that the specific command options and modules are compatible with your Linux distribution and kernel version. Different distributions may have variations in command syntax and module support, so test these commands in a safe environment before deploying them in production.
Why Firewalls are Essential
A firewall functions as a gatekeeper for your network, positioned between your systems and the outside world. It examines every incoming and outgoing network packet and decides whether to allow it through or block it. Without a firewall, your systems are exposed to various threats:
- Unauthorized Access Attempts: Hackers constantly scan for vulnerable systems to exploit.
- Denial-of-Service (DoS) Attacks: These attacks flood your system with requests, making it unusable.
- Malware: Viruses, worms, and Trojans can enter through open ports.
- Data Breaches: Sensitive information can be stolen if your systems are compromised.
A properly configured firewall provides your first line of defense against these threats.
Read: How to set up a UFW on Ubuntu 22.04
Core Firewall Tools in Linux
This guide focuses on three essential tools for firewall management:
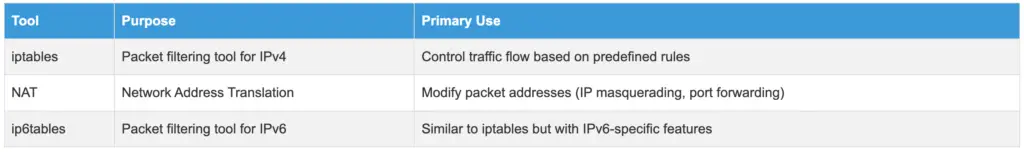
- iptables: Packet filtering tool for IPv4
- NAT: Network Address Translation
- ip6tables: Packet filtering tool for IPv6 (similar to iptables but with IPv6-specific features)
Understanding iptables
iptables is the command-line utility used to configure the Netfilter packet filtering framework built into the Linux kernel. The term “iptables” often refers to both the command itself and the underlying Netfilter framework.
Read: How to use NFS to Share remote files with Ubuntu 20.04
Key Concepts
Tables
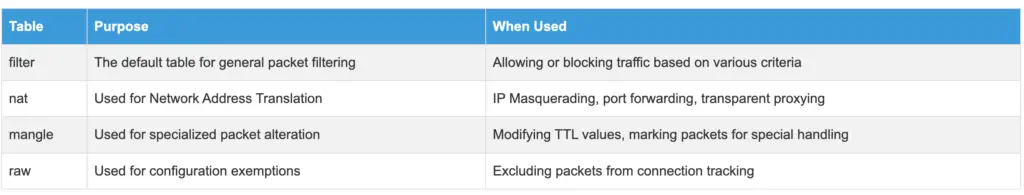
iptables uses different tables to organize rules, each responsible for a specific type of packet processing:
- filter: The default table for general packet filtering (allowing or blocking traffic)
- nat: Used for Network Address Translation, including IP Masquerading
- mangle: Used for specialized packet alteration (like modifying TTL values)
- raw: Used for configuration exemptions from connection tracking
Chains
Within each table, rules are organized into chains. Think of chains as checklists that the kernel consults when a packet arrives. The built-in chains are:
- INPUT: For packets destined for the local system itself
- OUTPUT: For packets originating from the local system
- FORWARD: For packets being routed through the local system
Rules
Each chain contains a list of rules specifying:
- Matching Criteria: What kind of packets does this rule apply to? (e.g., source IP address, destination port, protocol)
- Target: What to do with the packet if it matches the criteria (e.g., accept it, drop it, reject it)
Targets
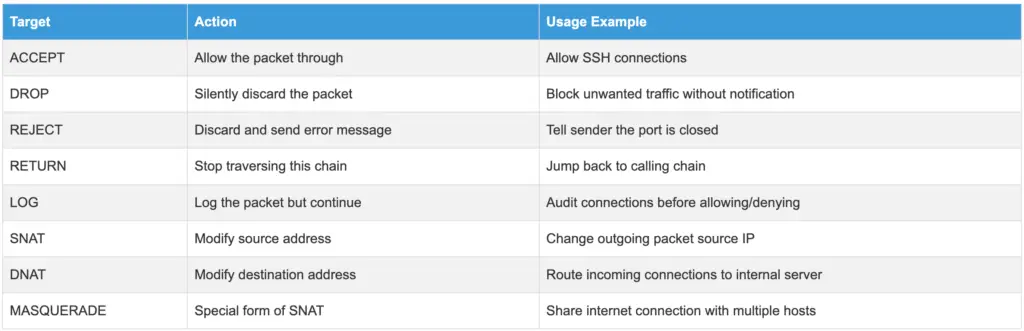
The most common targets are:
- ACCEPT: Allow the packet through
- DROP: Silently discard the packet (the sender gets no notification)
- REJECT: Discard the packet and send an error message back to the sender
- RETURN: Stop traversing this chain, go back to caller chain
- LOG: Log the packet but continue processing with next rule
- SNAT: Modify the source address of the packet (Source NAT)
- DNAT: Modify the destination address of the packet (Destination NAT)
- MASQUERADE: Special form of SNAT for dynamic IP addresses
Basic iptables Command Structure
iptables [-t table] -[action] chain rule-specification [options]
- -t table: Specifies the table to use (e.g., -t nat). If omitted, the filter table is used.
- -[action]: Specifies the action:
- -A (Append): Add a rule to the end of a chain
- -D (Delete): Delete a rule from a chain
- -C (Check): Check if a rule exists in a chain
- -I (Insert): Insert a rule at a specific position
- -R (Replace): Replace a rule at a specific position
- -L (List): List all rules in a chain
- -F (Flush): Delete all rules in a chain
- -P (Policy): Set the default policy for a chain
- chain: The chain to modify (e.g., INPUT, OUTPUT, FORWARD)
- rule-specification: The criteria for matching packets
- [options]: Additional options, such as -j to specify the target
Example:
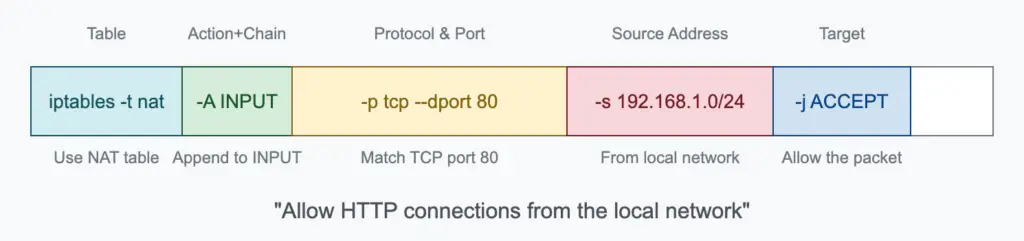
iptables -A INPUT -p tcp --dport 22 -j ACCEPT
This rule allows incoming SSH connections:
-A INPUT: Append this rule to the INPUT chain-p tcp: Match packets using the TCP protocol--dport 22: Match packets destined for port 22 (SSH)-j ACCEPT: If the packet matches, accept it
Common iptables Options
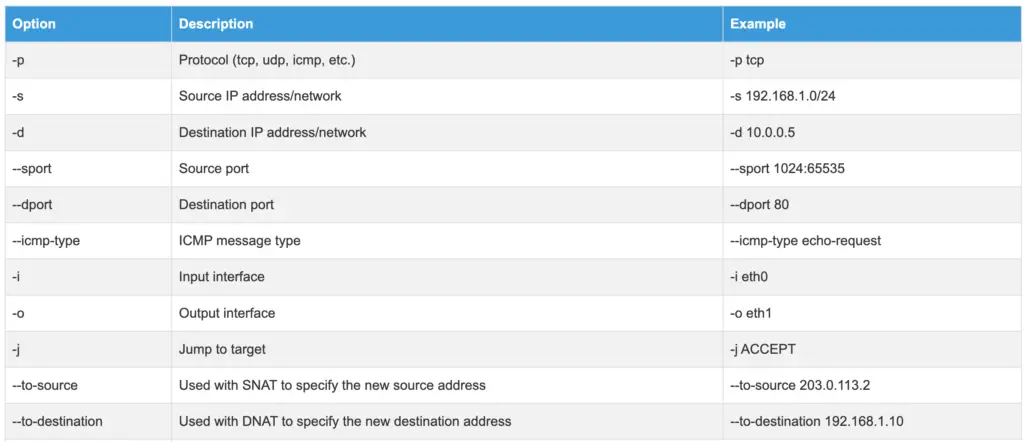
-p: Protocol (tcp, udp, icmp, etc.)-s: Source IP address/network-d: Destination IP address/network--sport: Source port--dport: Destination port--icmp-type: ICMP message type-i: Input interface-o: Output interface-j: Jump to target--to-source: Used with SNAT to specify the new source address--to-destination: Used with DNAT to specify the new destination address-n: Use numeric output (don’t resolve hostnames or port names)-v: Verbose output (includes packet and byte counters)
Read: How to install Apache web server on Ubuntu 22.04
Understanding ip6tables
ip6tables is the IPv6 counterpart to iptables, working almost identically but designed to handle IPv6 packets. Key differences include:
- IPv6-specific Protocol Options: ip6tables supports IPv6-specific protocol options like ICMPv6
- IPv6 Address Format: When specifying addresses, you must use IPv6 format
- Extension Headers: ip6tables can match on IPv6 extension headers
Example:
ip6tables -A INPUT -p ipv6-icmp --icmpv6-type echo-request -j ACCEPT
This rule allows ICMPv6 echo requests (ping6) to your system.
Best Practice for IPv6
Always configure both iptables and ip6tables when setting up your firewall. Many administrators focus only on IPv4 security, leaving their systems vulnerable via IPv6. Remember that modern operating systems prefer IPv6 when available, so securing only IPv4 is insufficient.
Extending Functionality with Modules
iptables is highly extensible through modules that add new matching criteria and targets:
- state/conntrack: Provides connection tracking (stateful firewalling)
- limit: Limits the rate of packets matching a rule (prevents DoS attacks)
- mac: Matches packets based on MAC address
- multiport: Allows specifying multiple ports in a single rule
- iprange: Matches a range of IP addresses
- string: Matches packets containing specific strings
- comment: Allows adding comments to rules for documentation
You load modules with the -m option:
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
This rule uses the state module to allow packets that are part of established or related connections.
Packet Filtering Techniques
Managing Rules and Chains
# Adding and changing rules
iptables -A chain rule-specification # Append a rule
iptables -D chain rule-specification # Delete a matching rule
iptables -D chain rulenum # Delete rule by number
iptables -I chain [rulenum] rule-spec # Insert a rule at position
iptables -R chain rulenum rule-spec # Replace a rule
iptables -L [chain] # List rules
iptables -F [chain] # Flush (delete) all rules
iptables -Z [chain] # Zero packet/byte counters
iptables -N chain # Create a new user-defined chain
iptables -X chain # Delete a user-defined chain
iptables -P chain target # Set default policy
User-Defined Chains
You can create custom chains to organize your rules more effectively:
# Create a new chain for HTTP rules
iptables -N HTTP_RULES
# Add rules to the new chain
iptables -A HTTP_RULES -s 192.168.1.0/24 -j ACCEPT
iptables -A HTTP_RULES -j DROP
# Jump to the new chain from INPUT chain
iptables -A INPUT -p tcp --dport 80 -j HTTP_RULES
This creates a chain that only allows HTTP traffic from the 192.168.1.0/24 network.
Connection Tracking with State Module
The state module allows iptables to track connection states:
- NEW: A packet starting a new connection
- ESTABLISHED: A packet that’s part of an existing connection
- RELATED: A packet related to an existing connection
- INVALID: A packet that doesn’t fit into any known connection
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
This essential rule allows responses to your outbound requests.
Controlling ICMP Traffic
Allow essential ICMP types but restrict others:
# Allow ping (echo-request)
iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPT
# Allow essential ICMP error messages
iptables -A INPUT -p icmp --icmp-type destination-unreachable -j ACCEPT
iptables -A INPUT -p icmp --icmp-type time-exceeded -j ACCEPT
iptables -A INPUT -p icmp --icmp-type parameter-problem -j ACCEPT
Controlling Port Access
Filter packets based on their destination port:
# Allow incoming HTTP connections
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
# Allow incoming HTTPS connections
iptables -A INPUT -p tcp --dport 443 -j ACCEPT
Rate Limiting
Use the limit module to restrict the rate of matching packets:
# Rate limit incoming ping requests
iptables -A INPUT -p icmp --icmp-type echo-request -m limit --limit 1/s --limit-burst 4 -j ACCEPT
iptables -A INPUT -p icmp --icmp-type echo-request -j DROP
This allows up to 1 ping per second, with a burst of up to 4, and drops any excess.
Specialized Connection Tracking
For protocols that are challenging to handle with firewalls:
# Load the connection tracking module for FTP
modprobe nf_conntrack_ftp
# Allow FTP connections
iptables -A INPUT -p tcp --dport 21 -m state --state NEW -j ACCEPT
Read: How to Configure Network Settings in Ubuntu 22.04
Network Address Translation (NAT)
NAT allows you to modify packet source or destination addresses as they pass through your firewall, commonly used for:
- IP Masquerading: Making multiple computers on a private network appear as one
- Port Forwarding: Directing incoming traffic to internal machines
- Transparent Proxies: Redirecting traffic to a proxy server
NAT Chains and Targets
NAT Chains:
- PREROUTING: Modify packets before routing decisions (DNAT)
- POSTROUTING: Modify packets after routing decisions (SNAT)
- OUTPUT: Alter locally generated packets
NAT Targets:
- SNAT: Changes the source address of packets
- DNAT: Changes the destination address of packets
- MASQUERADE: Special form of SNAT for dynamic IP addresses
- REDIRECT: Redirects connections to a local port
IP Masquerading
Enable multiple computers to share a single public IP address:
# Enable IP forwarding
echo 1 > /proc/sys/net/ipv4/ip_forward
# For permanent change, add to /etc/sysctl.conf:
# net.ipv4.ip_forward = 1
# Add masquerading rule
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
# Allow forwarded packets
iptables -A FORWARD -i eth1 -o eth0 -j ACCEPT
iptables -A FORWARD -m state --state ESTABLISHED,RELATED -j ACCEPT
Where eth0 is your external interface and eth1 is internal.
Masquerading Selected Hosts
iptables -t nat -A POSTROUTING -s 192.168.1.0/24 -o eth0 -j MASQUERADE
This only masquerades traffic from the 192.168.1.0/24 network.
Port Forwarding
Redirect incoming connections to internal hosts:
# Forward incoming HTTP requests to an internal web server
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j DNAT --to-destination 192.168.1.10:80
# Allow the forwarded traffic through the filter table
iptables -A FORWARD -p tcp -d 192.168.1.10 --dport 80 -j ACCEPT
Transparent Proxying
Redirect traffic to a proxy server without client configuration:
# Redirect all outgoing HTTP traffic to a local proxy
iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 80 -j REDIRECT --to-port 3128
# Allow the redirected traffic
iptables -A INPUT -p tcp --dport 3128 -j ACCEPT
Advanced Packet Manipulation: The Mangle Table
The mangle table handles specialized packet alterations:
# Increase the TTL of outgoing packets
iptables -t mangle -A POSTROUTING -o eth0 -j TTL --ttl-set 64
Saving and Restoring Rules
iptables rules are not persistent by default. Save them using:
Universal Method
# Save rules to a file
iptables-save > /etc/iptables.rules
# Restore rules from a file
iptables-restore < /etc/iptables.rules
Distribution-Specific Methods
Debian/Ubuntu:
apt-get install iptables-persistent
CentOS/RHEL:
service iptables save
Complete Firewall Script Example
#!/bin/bash
# Flush existing rules
iptables -F
iptables -X
iptables -t nat -F
iptables -t nat -X
iptables -t mangle -F
iptables -t mangle -X
# Set default policies
iptables -P INPUT DROP
iptables -P FORWARD DROP
iptables -P OUTPUT ACCEPT
# Allow loopback traffic
iptables -A INPUT -i lo -j ACCEPT
iptables -A OUTPUT -o lo -j ACCEPT
# Allow established and related connections
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
# Allow SSH (rate limited)
iptables -A INPUT -p tcp --dport 22 -m state --state NEW -m recent --set
iptables -A INPUT -p tcp --dport 22 -m state --state NEW -m recent --update --seconds 60 --hitcount 4 -j DROP
iptables -A INPUT -p tcp --dport 22 -m state --state NEW -j ACCEPT
# Allow HTTP and HTTPS
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
iptables -A INPUT -p tcp --dport 443 -j ACCEPT
# Allow essential ICMP
iptables -A INPUT -p icmp --icmp-type echo-request -j ACCEPT
iptables -A INPUT -p icmp --icmp-type time-exceeded -j ACCEPT
iptables -A INPUT -p icmp --icmp-type destination-unreachable -j ACCEPT
# Block invalid packets
iptables -A INPUT -m state --state INVALID -j DROP
# Log dropped packets
iptables -A INPUT -j LOG --log-prefix "IPTABLES DROP: " --log-level 4
# Save rules
iptables-save > /etc/iptables.rules
echo "Firewall rules have been applied."
This script:
- Allows SSH, HTTP, and HTTPS access
- Permits essential ICMP traffic
- Blocks everything else
- Implements basic protection against common attacks
Monitoring and Logging
Monitor your firewall for security and troubleshooting:
# Log SSH access attempts
iptables -A INPUT -p tcp --dport 22 -j LOG --log-prefix "SSH ACCESS: " --log-level 4
# View logs
tail -f /var/log/syslog | grep "IPTABLES"
# On systems using systemd's journal
journalctl -f | grep "IPTABLES"
Best Practices for Linux Firewalls
- Default Deny Policy: Start with a default deny policy and explicitly allow only necessary traffic
- Minimize Open Ports: Absolutely necessary and Only open ports
- Use Stateful Inspection: Always use connection state tracking for return traffic
- Rate Limit: Implement rate limiting for services like SSH to prevent brute force attacks
- Secure IPv6: Configure both IPv4 and IPv6 firewalls
- Regular Updates: Keep your firewall rules updated as services change
- Implement Logging: Log suspicious activities
- Backup Rules: Maintain backups of your firewall configurations
- Test Configurations: Always test rules in a safe environment first
- Document Everything: Keep clear documentation of your firewall setup
Conclusion
Mastering iptables, ip6tables, and NAT is essential for Linux administrators. These tools provide powerful packet filtering and network address translation capabilities that form the foundation of Linux network security. Understanding tables, chains, rules, and targets enables you to create effective and secure firewall configurations.
Remember that firewall configuration is just one part of a comprehensive security strategy. It should be combined with regular updates, strong authentication, intrusion detection, and security monitoring.
Frequently Asked Questions
General Questions
What is the difference between iptables and nftables? nftables is the modern successor to iptables, introduced in Linux kernel 3.13. It offers improved performance, more consistent syntax, and better scalability. While iptables remains widely used, nftables represents the future of Linux packet filtering.
Do I need a firewall if I’m behind a router? Yes, even behind a router with NAT, a host-based firewall provides an additional security layer. Your router might not protect against attacks from other devices on your local network or from malware.
How do I check if iptables is running?
sudo iptables -L
If it returns a list of rules, iptables is active. An error may indicate you need to install or load the iptables module.
Configuration Questions
Why won’t my service work after setting up my firewall? The most common reason is forgetting to allow required ports. Check your service’s documentation for necessary ports and ensure they’re allowed in your rules.
How do I allow multiple ports in a single rule? Use the multiport module:
iptables -A INPUT -p tcp -m multiport --dports 80,443,8080 -j ACCEPT
How do I back up and restore iptables rules?
# Backup
sudo iptables-save > /path/to/backup/file
# Restore
sudo iptables-restore < /path/to/backup/file
Advanced Questions
Can I block specific websites with iptables? Yes, but it’s not straightforward. You can block by IP address, but this is ineffective for sites using shared hosting. A DNS-based blocking solution or proxy server works better.
How do I implement QoS with iptables? Use the mangle table with the tc (traffic control) subsystem. This requires additional configuration beyond basic iptables rules.
How do I protect against SYN flood attacks?
iptables -A INPUT -p tcp --syn -m limit --limit 1/s --limit-burst 3 -j ACCEPT
iptables -A INPUT -p tcp --syn -j DROP
How do I troubleshoot iptables rules? Add LOG rules before DROP rules:
iptables -A INPUT -j LOG --log-prefix "DROPPED: " --log-level 4
iptables -A INPUT -j DROP
Check system logs for entries with the “DROPPED” prefix.
Migration Questions
How do I migrate from iptables to nftables? Most distributions provide conversion tools. In Debian/Ubuntu:
iptables-translate -A INPUT -p tcp --dport 22 -j ACCEPT
This outputs the equivalent nftables command.
Will my existing iptables scripts work with UFW or FirewallD? Not directly. UFW and FirewallD are higher-level management tools for iptables/nftables. You’ll need to convert your rules to use their specific syntax.
If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.