The sudoers file is used by Linux and Unix administrators in general in order to to allocate specific system rights to new and existing system users. This enables the system administrator to control what every user does in order to ensure they would not interfere with the system files or processes. Since most Linux distros are built with security in mind, when a user wants to run a command in the terminal that requires root privileges, the system will check the username against the sudoers file.
In this article we will try to explain the different fields that are found in the file /etc/sudoers.
If you run the command :
sudo visudo
The following file will show up :
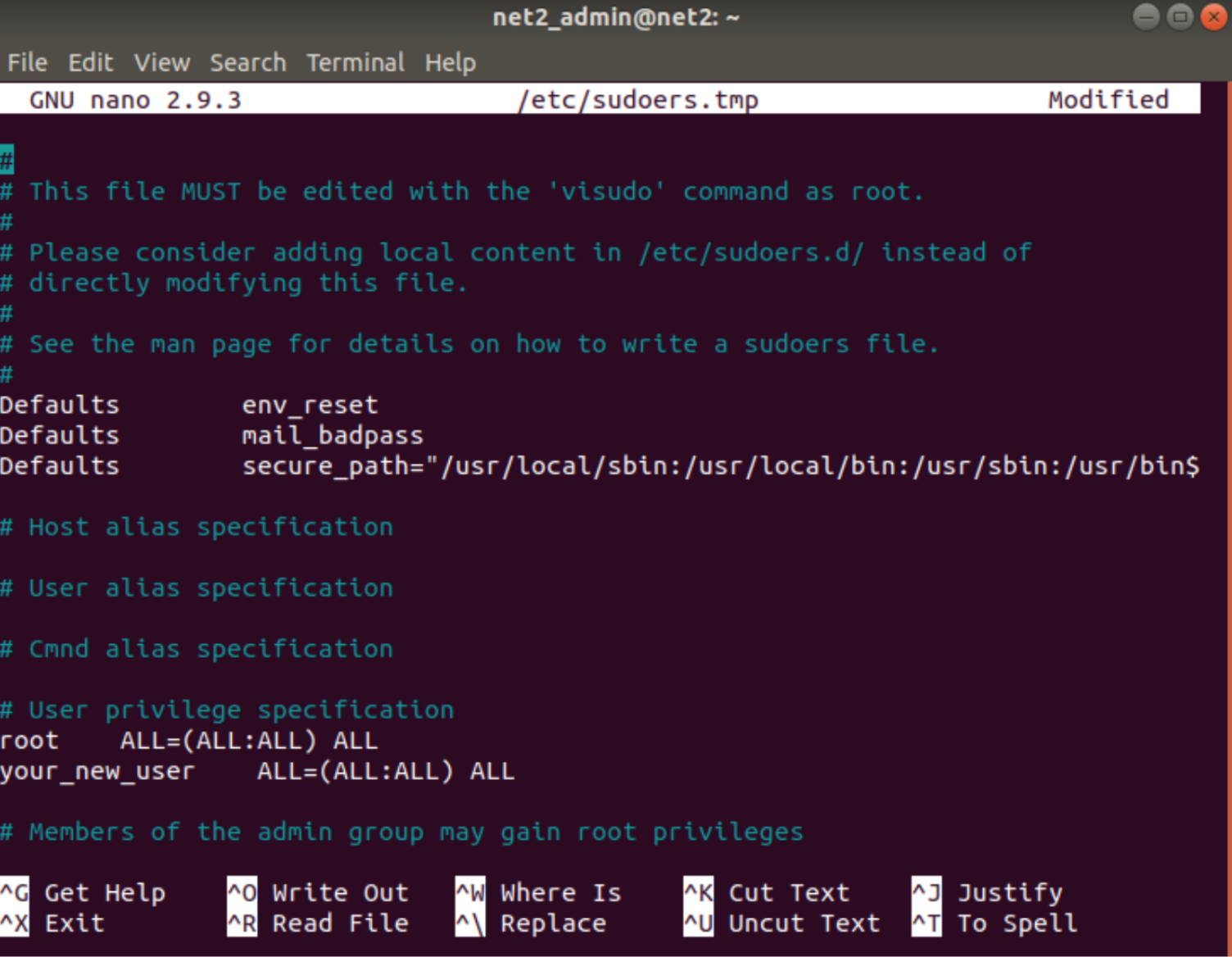
sudoers example
As you can see, there are many lines in the file that require an explanation. We will try to discuss this in the following paragraphs.
Default variables section
![]()
Since program behavior can be influenced by environment variables, sudoers allows to restrict which user’s environment variables are inherited by the command to be invoked.
The first line above that starts with “Defaults env_reset”, which is enabled by default, , resets the terminal environment in order to remove any user variables. This is a safety precaution used to remove any potentially dangerous environmental variables which might exist in the sudo session. In other words, commands will be run with a minimal, new environment.
![]()
In the second line, we find the statement ‘Defaults mail_badpass’. This is used to
Send a notice to the configured mailto user if a wrong password has been entered by the user running sudo. By default,this flag is off.
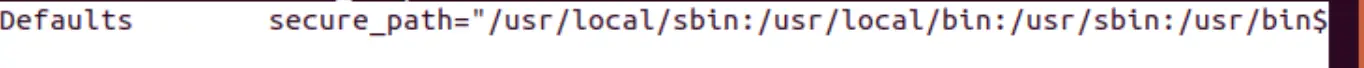
This displays the path (locations where the system will look for application) used for for all commands which are run from sudo. Administrators may want to use this if the sudo users they create are not trustworthy enough to have a clean PATH environment variable. This can also be used in case you want to separate the “root path” from the ”user path”. This option is not set by default.
You may be interested to read: How to create a Sudo user on Ubuntu
User privilege section

The root user’s sudo privileges are defined in this section which is completely different from the preceding one. We will now explain the meaning of the different fields:
![]()
The rule will apply to the first field above which is the username. Here it has the value of ‘root’ .
![]()
The first “ALL” highlighted above, shows that this rule will apply to all hosts.
![]()
The user is able to run commands as all users as indicated by this second “ALL”.
![]()
The third “ALL” means that the corresponding user is able to run commands as all groups.
![]()
The last “ALL” means that these rules will apply to all commands. The values above indicate that the corresponding user will be able to run any command with sudo (if they use their password).
Read: How to manage permissions in Linux – guide for beginners
Group privilege section
![]()
This section defines groups’ sudo rules. The words which begin with a “%” sign, indicate group names. ![]() From the snapshot above, we can tell that the “admin” group will be able to execute any command as any other user on any host.
From the snapshot above, we can tell that the “admin” group will be able to execute any command as any other user on any host.
![]() In a similar fashion, the sudo group will behave like the admin group above.
In a similar fashion, the sudo group will behave like the admin group above.
/etc/sudoers.d section
The line above which begins with a # sign, which might appear like a comment, indicates that files within the directory /etc/sudoers.d will be sourced and accounted for as well.
The same rules govern the /etc/sudoers file will also apply to the files within the /etc/sudoers.d directory as well.
Any file that does not have a . in it and does not end in ~ will be read by sudo in order to avoid causing issues with package manager.
You may be interested to read: How to add and delete users on Ubuntu/Debian
The order with which sudo will read the files is a lexical order, for instance, /etc/sudoers.d/10_second will be parsed after the file /etc/sudoers.d/01_first. Note that since the order is not numeric, /etc/sudoers.d/10_second would be read before /etc/sudoers.d/1_whoops
Note that the files in a #includedir directory will not be edited by visudo unless at least one of them has a syntax error. This is unlike files embedded using #include.
Since visudo is used to edit the /etc/sudoers file, it can also be invoked to edit files in the /etc/sudoers.d directory as well.
The syntax to do so would be as follows:
- sudo visudo -f /etc/sudoers.d/file_to_edit
Other files inclusion from within sudoers
Using the #include and #includedir directives, it is possible to include other files alongside other sudoers from within the sudoers file. This is useful for instance to keep , in addition to a local per machine file, a site wide sudoers file.
For instance the side wide file is /etc/sudoers and the local per machine file will be /etc/sudoers.local. You would need to use the directive below in order to include the /etc/sudoers.local from within the /etc/sudoers :
#include /etc/sudoers.local
Once sudo reads this line, it will stop processing (or suspend) the file /etc/sudoers and switches immediately to /etc/sudoers.local. When the last line of /etc/sudoers.local has been read by sudo, it will resume the processing of /etc/sudoers file where it left off.
Included files may themselves include other files, up to 128 nested files can be supported.
If the path to the added include file does not begin with a “/” sign, i.e. is not fully qualified, it must reside in the same folder as the sudoers file from which it is called (.i.e. it was included from). For instance if the line
#include sudoers.local
Is added to /etc/sudoers, then /etc/sudoers.local is the file that will be include.
If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.