The DoS ( Denial Of Service ) attack, also known as denial of service attack, is an attempt to cause an overload on a common server or computer so that system resources are unavailable to its users. For this, the attacker uses techniques by sending several packet requests to the target in order to make it so overloaded that it can no longer respond to any packet request. Thus, users are no longer able to access computer data because it is unavailable and unable to respond to any request.
The most common targets of denial of service attacks are web servers. With the attack, the hacker or cracker tries to make the hosted pages unavailable on the Web. This attack is not characterized as an invasion of the system since it only performs the invalidation through overload.
Credits: safetydetectives
Attackers often obstruct the communication media between users and the system in order not to communicate properly. Another way to carry out the attack is to force the victim to reboot or consume all memory, processing or other hardware resources in such a way as to make him unable to provide the service.
DoS attacks involve only one attacker, with a single computer making multiple packet requests to the target. In this type of attack, the hacker can only take down weak servers and ordinary computers with low bandwidth and low technical specifications.
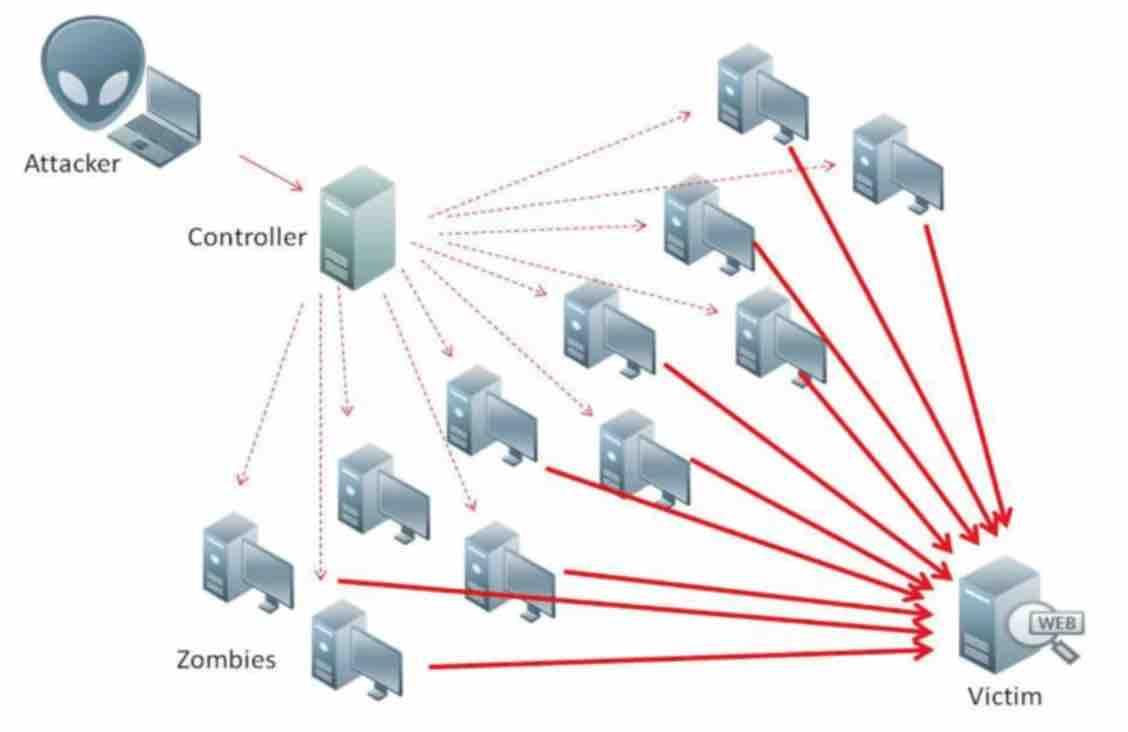
What is DDos attack ?
In the distributed denial of service attack , known as DDoS ( Distributed Denial of Service , in English), a master computer can manage up to millions of computers, called zombies.
Read: Your worst nightmare, Malware on Android devices
Through DDos service , the master computer enslaves several machines and makes them access a given resource on a given server all at the same time. Thus, all zombies access together and uninterruptedly the same resource as a server. Taking into account that the web servers have a limited number of users that can be served at the same time, this large number of traffic makes it impossible for the server ( without a DDos protection) to be able to fulfill any request. The server can restart or even hang depending on the resource that was victimized.
There are several tools used by hackers to make continuous packet requests for various protocols. One of them, is the T50 Sukhoi PAK FA Mixed Packet Injector, which allows the attacker to attack the server.
Although trojans used for this type of attacks are uncommon and difficult to detect, it is still possible to know whether a computer is part of a DDoS attack system and dependent on a master computer. For this, it is necessary for the user to be aware of the network traffic to which his computer or server is connected. If the computer is sending packages without the user accessing any service on the Internet, this could be an indication that the machine is a zombie. Also, the Internet can be slow even without performing several simultaneous tasks on the network
If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.
