By Harikrishna Kundariya – Laravel is an open-source development platform that contains a PHP framework, which is one of the most used scripting languages of the 21st century. In spite of its numerous advantages, most Laravel development Agencies are still looking for ways to make the platform and applications made from it more secure.
Laravel has a good name for assurance to protect the website and applications. However, if any potential loophole is detected, a capable team within Laravel is always ready to take care of it promptly. Furthermore, there are multiple ways to improve the security of Laravel as no framework can ever claim to have guaranteed security.
With the growing popularity and prominence of Laravel, it is crucial to understand the ways to secure the website and applications. Therefore, in this article, we will talk about the Top effective Laravel-based security practices that as a developer you should know to ensure full security!
Read: Web Development Vs. Software Development, Which is the better career
Top 7 Laravel Security Practices a developer Should Know:
Avoid raw queries to Prevent SQL injections
Typically, a web application deals with a database to receive user input, or to show the users some information. SQL injection attacks can be carried out when a user enters some input for SQL query, hence it becomes extremely important to have safeguards against it.
Hence, to prevent such attacks, Laravel uses PDO binding, which ensures that no variable is passed on to the database without proper validation. Thus, on receiving random inputs, an error message is displayed. Still, developers might tend to go for raw SQL, for various personal reasons.
If you are one of those developers, make sure that you use well-prepared SQL queries to prevent such mishaps. For example, the following code-snippet has a huge vulnerability for SQL injection:
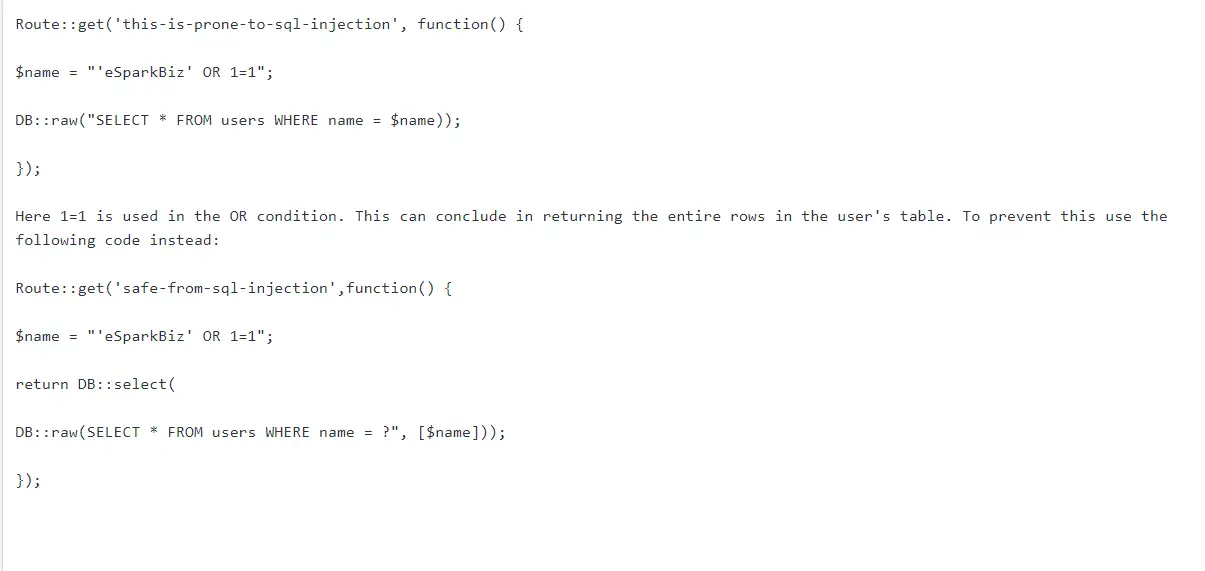
Now, what Laravel will do is that it will replace the question marks with the query variables. This results in automatically bypassing the input variable. Also, it will remove the inherent vulnerability of code to SQL injection attacks.
Read: 10 Most Common Applications with Elegant Syntax from Laravel
Make sure to use the HSTS protocol, if your application deals with sensitive data.
With the growing technical developments, many advanced web security policies are erupting in the IT industry. HSTS (HTTP Strict Transport Security) is one of those web security that compels web browsers to interact with authorized websites only. It uses fortified and secure HTTPS connections only.
Read: HTTP or HTTPS: What’s the Difference and Which One is Better to Use
In HTTP websites, any data sent to the backend is sent in plain format, it is not encrypted at all. Thus, any malicious third party can intercept the requests and steal sensitive data like passwords, card details, etc. That is where the “S” (secure) of HTTPS comes into the picture because the HTTPS protocol encrypts all data before it is sent.
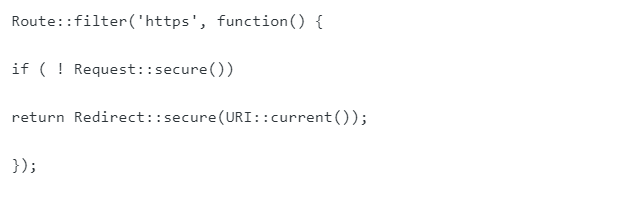
Transitioning from HTTP to HTTPS requires an SSL certificate for the website, which is pretty easy, and you can always take help from a seasoned developer for the same. Additionally, to hide certain routes, following a code-snippet will suffice as it redirects users to a better-secured route.
Escape content to prevent cross-site scripting (XSS) attacks.
Cross-Site Scripting (XSS) attacks are a type of injection. Here the harmful scripts are injected into other well-organised and trusted websites. It can be avoided if you use double-brace syntax in the blade templates à ({{ $variable }})
However, if you are sure that the data in the above variable is safe to be displayed, you can use {!! $variable !!} syntax.
Use HTML Purifier.
Purifier itself means to clean the unwanted access in the server. To ensure that no raw HTML is produced for the customer, Laravel uses double-braced syntax. However, you might want to generate some HTML variables from your database for your customer. If that is the case, you can use the HTML Purifier (written in PHP). It will remove all malicious code with a thoroughly audited, secure yet permissive whitelist.
Read: Top 7 Programming Languages to Learn
Entrusted CSRF protection:
CSRF protection is quite a traditional method to filter the request and provide access only to the authorized users. It is simply cross-site request forgery that detects the unauthorized request to enter your server. Here, the Form Classes Token Method is used within the source code of Laravel. As a result, Laravel has enabled this method by default on its server.
You can have the token and an inbuilt CSRF filter embedded in your source code. With the help of this term, you can rest assured to be safe from the involvement of hackers. If a CSRF filter detects any potential XSS attack by a third party, it immediately returns the HTTP 500 error and denies access to them.
Timely Update your packages, plugins, and modules
It is highly recommended to update the security practice of Laravel plugins and modules frequently. This brings the latest security fixes and algorithmic enhancements. Through the updates, the deprecated and obsolete library functions are removed, and new ones with improved performance and added functionalities are made available to you.
Similarly, the complexity of cyber-attacks is also evolving with each passing day. If you continue to stick with older versions and modules, your website becomes an easy target for cyber-attacks. By this, you might have to face serious consequences, as such attacks can steal valuable data, or hack your servers leading to huge losses.
Therefore, it is of paramount importance to be armoured with the latest security tools available out there.
Use Powerful Cookies.
By this, Laravel will make sure that your cookies are secured and bullet-proof. It provides you to create and enable the encryption key.
Now you just need to add the key to the app.php file in the config folder but only if you are working on versions 5 and above. If you are working on version 3 and below, add the application.php file in your config directory.
Additional Tips of Laravel Security Practices:
In the list of Top 7 Laravel Security Practices, a developer should also know the basic practices to secure the server effectively.
- Use the hash password method. Jumble the passwords by using a modified salted hashing function. Through this function, the processor power increases which results in improving the work factor. Laravel, by default, supports both Bcrypt and Argon2 hashing functions.
- Focus on Laravel’s API. It allows you to access an overall collection of databases and most prominent files that are enabled by default in the config/session.php files as well as cookies.
- Use the .env parameter MAIL_DRIVER=log to save all your emails into storage/logs/laravel.log file. By this, you can test email contents in your app rather than being sent.
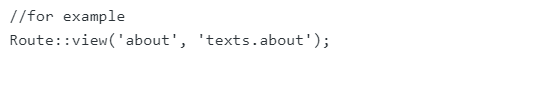
- Use Route::view() function to show a certain view rather than creating a Controller method.
Read: 8 Skills Needed To Become A Hirable NodeJs Developer
Conclusion:
Laravel is definitely a state-of-the-art web development framework. Also, it is highly popular and comes loaded with powerful features. However, an application can never be fool-proof and immune from all kinds of threats out there.
Other than the above list of top Laravel security practices, there is a lot more, which, as a developer, you should know and implement to secure the application. A comprehensive understanding of present-day threats can certainly reveal deeper vulnerabilities so they can be well guarded and the application be well armoured for any incoming attack. Till then, be a responsible coder and ensure that you check all the points mentioned above for well-protected application architecture.
Happy coding!
Harikrishna Kundariya, a marketer, developer, IoT, ChatBot & Blockchain savvy, designer, co-founder, Director of eSparkBiz Technologies. His 8+ experience enables him to provide digital solutions to new start-ups based on IoT and ChatBot. harikrishna.kundariya[@]esparkbiztechnologies.com

If you like the content, we would appreciate your support by buying us a coffee. Thank you so much for your visit and support.



